Caught in the Act: Uncovering SpyNote in Unexpected Places
Published on
Published on
Published on
Jun 20, 2024
Jun 20, 2024
Jun 20, 2024





Introduction
In hidden corners of the Internet, open directories often serve as treasure troves, offering a glimpse into the unguarded secrets of digital repositories. While sometimes mundane, these directories can occasionally reveal attention-grabbing discoveries.
Our team recently unearthed multiple samples of SpyNote, a well-known spyware targeting Android devices, cleverly disguised as legitimate apps such as Google Translate, Temp Mail, Deutsche Postbank, and even an app supposedly meant to discourage intoxicated driving.
This finding highlights how innocuous-seeming servers can often host dangerous threats. To stay protected, apply for a demo on Hunt and proactively access up-to-date threat information.
What is SpyNote, and How Does it Operate?
SpyNote is a sophisticated piece of malware that, as the name suggests, emphasizes spying on its victims. It has become a significant threat to Android users, especially after its source code was leaked in late 2022.
The spyware exploits accessibility services and device administrator privileges, allowing the malicious software to steal sensitive information such as device location, contacts, SMS messages, etc.
SpyNote samples routinely use deception, disguising itself by using legitimate app icons to trick users into believing it is a harmless application while silently collecting their data.
For further information on the technical analysis of SpyNote, check out the following articles:
Fortinet – Android/SpyNote Moves to Crypto Currencies
McAfee – Android SpyNote attacks electric and water public utility users in Japan
ThreatFabric – SpyNote: Spyware with RAT capabilities targeting Financial Institutions
Our Discoveries: SpyNote Samples in OpenDirs
The Hunt platform provides hundreds of tags for known malware families and open-source tools in open directories, including SpyNote, as shown in Figure 1.
 Figure 1: Tags for SpyNote samples in open directories
Figure 1: Tags for SpyNote samples in open directoriesUsers can navigate directly to a page listing all the latest SpyNote samples hosted on misconfigured servers by clicking on any of these tags. In Figure 2, you’ll see that the historical data for discovered .apk files covers the past two months, providing an overview of the spyware’s recent activity. This tagging system ensures users can quickly track and analyze the presence of SpyNote and other threats across various open directories.
 Figure 2: Result of clicking on the SpyNote tags. Try it!
Figure 2: Result of clicking on the SpyNote tags. Try it!Let's examine some particularly interesting samples we've found and their connections to Command and Control (C2) infrastructure.
Translate.apk
This directory, hosted on AWS at IP 18.219.97_209:8081, contained just three files: Google.apk, Translate.apk, and desktop.ini. Curiously, the first two files are identical, only differing in name.
Upon installation, the app perfectly mirrors the legitimate Google Translate application, but a likely developer slip-up stands out. When requesting accessibility permissions, the instructions read “- Enable [MY-NAME],” a placeholder that should have been replaced. This error is shown in Figure 3.
 Figure 3: Accessibility services request screen (Source: Hatching Triage)
Figure 3: Accessibility services request screen (Source: Hatching Triage)At the same time, the malicious app starts making network requests to its C2, kyabhai.duckdns_org, hosted on the same IP address at port 8080.
Directory Details
Open Directory & C2 IP: 18.219.97_209:8081
Googe.apk & Translate.apk SHA-1 hash: 3aad911b21907053a69b49086a6396c50714accb
C2 domain: kyabhai.duckdns_org:8080
Triage Link: https://tria.ge/240617-lwchbavhme
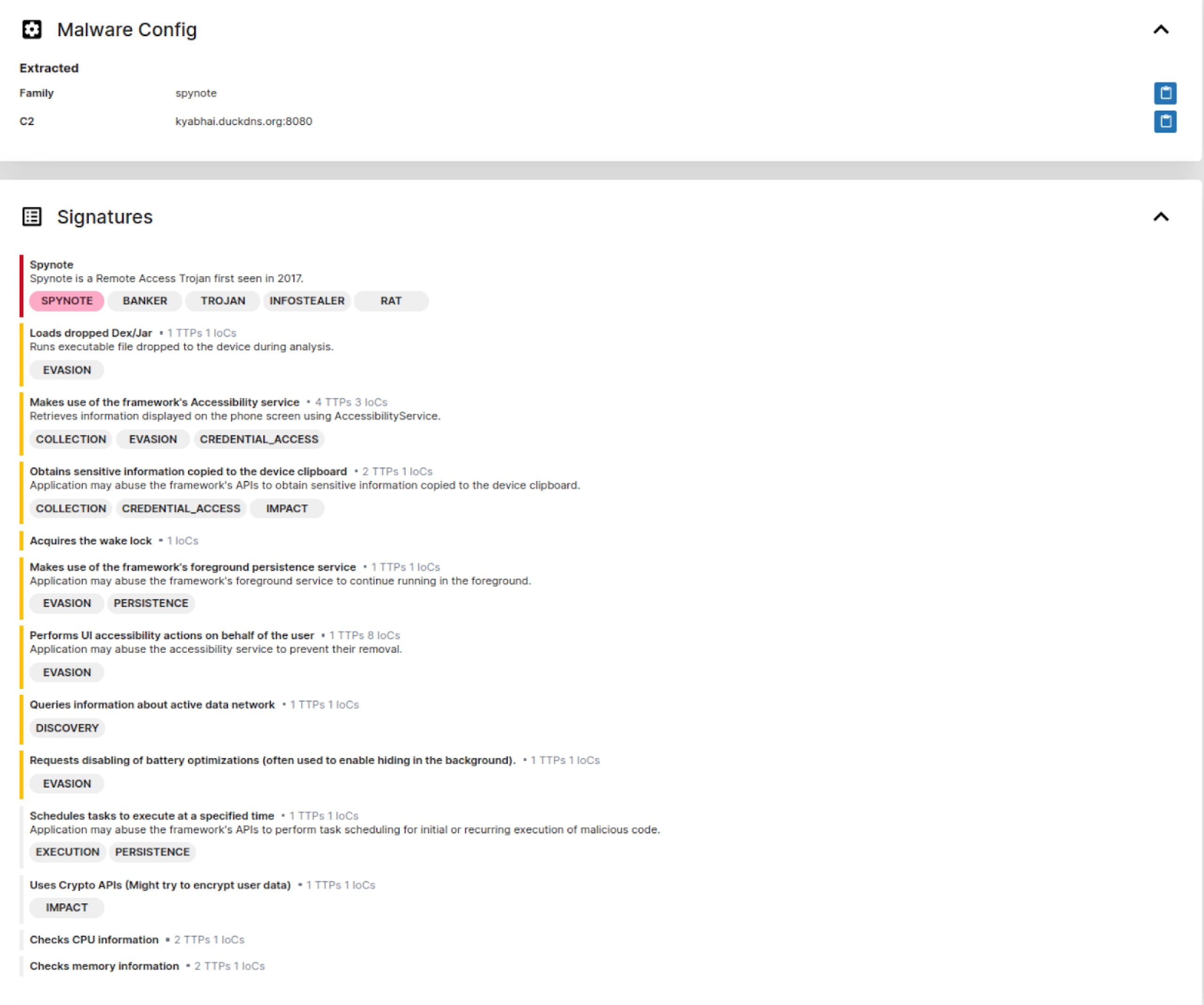 Figure 4: File metadata for Translate.apk (Source: Hatching Triage Sandbox )
Figure 4: File metadata for Translate.apk (Source: Hatching Triage Sandbox )Temp_20Mail.apk
Moving on, we explored an open directory hosted by SonderCloud Limited at IP 156.245.13_61:8000. This directory not only contained several SpyNote APKs but also hosted Cobalt Strike and Sliver binaries targeting the Windows operating system.
Among these, a file named "Temp_20Mail.apk" caught our eye. This file disguises itself as the legitimate Temp Mail app, which allows users to generate disposable email addresses. However, unlike the previous samples, once installed, this program begins beaconing to the C2 IP address 156.245.20_17:7771.
Figure 5 displays the malicious app using the legitimate icon, while Figure 6 shows the Temp Mail app on the Google Play Store.
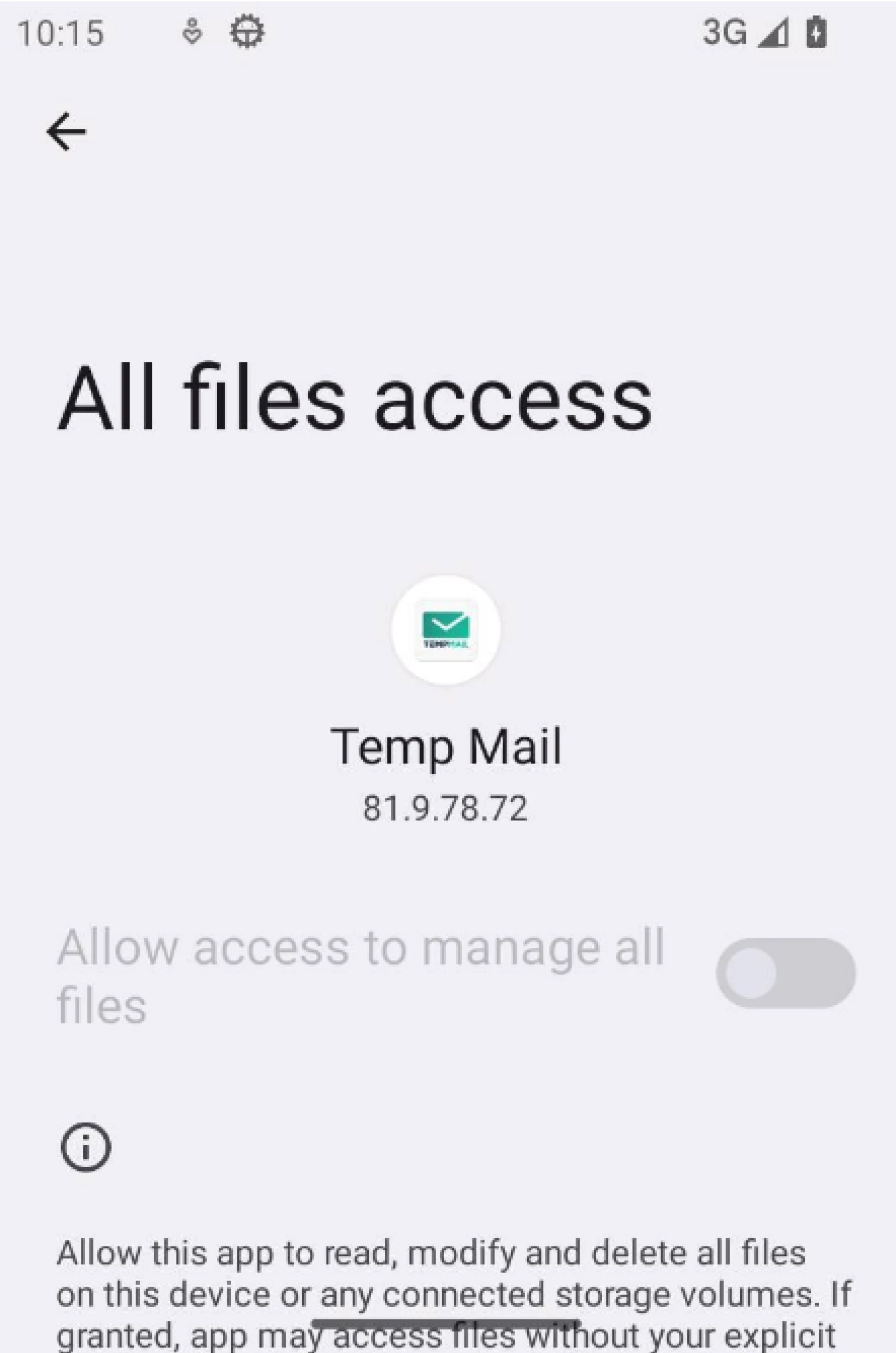 Figure 5: Screenshot of the malicious Temp Mail application
Figure 5: Screenshot of the malicious Temp Mail application Figure 6: Legitimate Temp Mail app in the Google Play Store
Figure 6: Legitimate Temp Mail app in the Google Play StoreAdditional information on the C2 was limited, but we did discover that the IP recently resolved to two domains: gw.585822_vip and nerjowmqw_com.
Directory Details
Open Directory: 156.245.13_61:8000
C2: 156.245.20_17:7771
Temp_20Mail.apk SHA-1 hash: 5b9bfa06d05172f61d1ee19724fcd12cec110353
Triage Link: https://tria.ge/240617-l875rawdph/behavioral2
 Figure 7: Metadata for Temp_20Mail.apk (Source: Hatching Triage Sandbox)
Figure 7: Metadata for Temp_20Mail.apk (Source: Hatching Triage Sandbox)postbank.apk
The following file masquerades as an app for the German bank Post Bank. This app communicates with the domain oebonur600.duckdns_org, which resolves to IP address 95.214.177_114 on port 3210 in a pattern that's becoming alarmingly familiar.
A screenshot of the app during dynamic analysis is provided in Figure 8, showcasing its deceptive interface.
 Figure 8: Screenshot of postbank.apk during dynamic analysis (Source: Hatching Triage Sandbox )
Figure 8: Screenshot of postbank.apk during dynamic analysis (Source: Hatching Triage Sandbox )The C2 is hosted on Cloudflare London at the Yusuf Kemal TURKMENOGLU ASN.
 Figure 9: IP Overview for C2 in Hunt
Figure 9: IP Overview for C2 in HuntIn late May 2024, a web page hosted on port 80 of the C2 contained the defacement message "HACKED BY PersoDev." This page included a JavaScript script that turned off the right-click context menu and displayed an alert message. Additionally, it featured CSS to alter the opacity of images with a hover effect.
We don’t believe the two are related, but it is an interesting finding.
 Figure 10: Screenshot of ports and protocols for the associated IP in Hunt. Try it out!
Figure 10: Screenshot of ports and protocols for the associated IP in Hunt. Try it out!Directory Details
Open Directory & C2 IP: 5.252.74.45_443
postbank.apk SHA-1 hash: dc9a821f1e061098188503dbf7518bf263334fcd
C2 domain: oebonur600.duckdns_org
Triage Link: https://tria.ge/240617-mhv8yawgqb
Impacts on Users and Devices
The discovery of SpyNote samples in open directories poses significant risks to users, as these malicious files utilize additional infrastructure, including dynamic domains, for data exfiltration.
Once infected, users' sensitive information can be continuously siphoned to ever-changing locations, making detection and mitigation more challenging.
Conclusion
The SpyNote samples we've discussed show how even everyday apps like Google Translate and Temp Mail can be repurposed for malicious intent. These examples are just a handful of the over 40 SpyNote APKs available in Hunt, with many more likely operating undetected and stealing sensitive information.
To stay ahead of these threats, apply for a free demo of Hunt. Track and analyze numerous threats identified in open directories, analyze the infrastructure of over 80 malware families, and effectively protect your digital environment.

Introduction
In hidden corners of the Internet, open directories often serve as treasure troves, offering a glimpse into the unguarded secrets of digital repositories. While sometimes mundane, these directories can occasionally reveal attention-grabbing discoveries.
Our team recently unearthed multiple samples of SpyNote, a well-known spyware targeting Android devices, cleverly disguised as legitimate apps such as Google Translate, Temp Mail, Deutsche Postbank, and even an app supposedly meant to discourage intoxicated driving.
This finding highlights how innocuous-seeming servers can often host dangerous threats. To stay protected, apply for a demo on Hunt and proactively access up-to-date threat information.
What is SpyNote, and How Does it Operate?
SpyNote is a sophisticated piece of malware that, as the name suggests, emphasizes spying on its victims. It has become a significant threat to Android users, especially after its source code was leaked in late 2022.
The spyware exploits accessibility services and device administrator privileges, allowing the malicious software to steal sensitive information such as device location, contacts, SMS messages, etc.
SpyNote samples routinely use deception, disguising itself by using legitimate app icons to trick users into believing it is a harmless application while silently collecting their data.
For further information on the technical analysis of SpyNote, check out the following articles:
Fortinet – Android/SpyNote Moves to Crypto Currencies
McAfee – Android SpyNote attacks electric and water public utility users in Japan
ThreatFabric – SpyNote: Spyware with RAT capabilities targeting Financial Institutions
Our Discoveries: SpyNote Samples in OpenDirs
The Hunt platform provides hundreds of tags for known malware families and open-source tools in open directories, including SpyNote, as shown in Figure 1.
 Figure 1: Tags for SpyNote samples in open directories
Figure 1: Tags for SpyNote samples in open directoriesUsers can navigate directly to a page listing all the latest SpyNote samples hosted on misconfigured servers by clicking on any of these tags. In Figure 2, you’ll see that the historical data for discovered .apk files covers the past two months, providing an overview of the spyware’s recent activity. This tagging system ensures users can quickly track and analyze the presence of SpyNote and other threats across various open directories.
 Figure 2: Result of clicking on the SpyNote tags. Try it!
Figure 2: Result of clicking on the SpyNote tags. Try it!Let's examine some particularly interesting samples we've found and their connections to Command and Control (C2) infrastructure.
Translate.apk
This directory, hosted on AWS at IP 18.219.97_209:8081, contained just three files: Google.apk, Translate.apk, and desktop.ini. Curiously, the first two files are identical, only differing in name.
Upon installation, the app perfectly mirrors the legitimate Google Translate application, but a likely developer slip-up stands out. When requesting accessibility permissions, the instructions read “- Enable [MY-NAME],” a placeholder that should have been replaced. This error is shown in Figure 3.
 Figure 3: Accessibility services request screen (Source: Hatching Triage)
Figure 3: Accessibility services request screen (Source: Hatching Triage)At the same time, the malicious app starts making network requests to its C2, kyabhai.duckdns_org, hosted on the same IP address at port 8080.
Directory Details
Open Directory & C2 IP: 18.219.97_209:8081
Googe.apk & Translate.apk SHA-1 hash: 3aad911b21907053a69b49086a6396c50714accb
C2 domain: kyabhai.duckdns_org:8080
Triage Link: https://tria.ge/240617-lwchbavhme
 Figure 4: File metadata for Translate.apk (Source: Hatching Triage Sandbox )
Figure 4: File metadata for Translate.apk (Source: Hatching Triage Sandbox )Temp_20Mail.apk
Moving on, we explored an open directory hosted by SonderCloud Limited at IP 156.245.13_61:8000. This directory not only contained several SpyNote APKs but also hosted Cobalt Strike and Sliver binaries targeting the Windows operating system.
Among these, a file named "Temp_20Mail.apk" caught our eye. This file disguises itself as the legitimate Temp Mail app, which allows users to generate disposable email addresses. However, unlike the previous samples, once installed, this program begins beaconing to the C2 IP address 156.245.20_17:7771.
Figure 5 displays the malicious app using the legitimate icon, while Figure 6 shows the Temp Mail app on the Google Play Store.
 Figure 5: Screenshot of the malicious Temp Mail application
Figure 5: Screenshot of the malicious Temp Mail application Figure 6: Legitimate Temp Mail app in the Google Play Store
Figure 6: Legitimate Temp Mail app in the Google Play StoreAdditional information on the C2 was limited, but we did discover that the IP recently resolved to two domains: gw.585822_vip and nerjowmqw_com.
Directory Details
Open Directory: 156.245.13_61:8000
C2: 156.245.20_17:7771
Temp_20Mail.apk SHA-1 hash: 5b9bfa06d05172f61d1ee19724fcd12cec110353
Triage Link: https://tria.ge/240617-l875rawdph/behavioral2
 Figure 7: Metadata for Temp_20Mail.apk (Source: Hatching Triage Sandbox)
Figure 7: Metadata for Temp_20Mail.apk (Source: Hatching Triage Sandbox)postbank.apk
The following file masquerades as an app for the German bank Post Bank. This app communicates with the domain oebonur600.duckdns_org, which resolves to IP address 95.214.177_114 on port 3210 in a pattern that's becoming alarmingly familiar.
A screenshot of the app during dynamic analysis is provided in Figure 8, showcasing its deceptive interface.
 Figure 8: Screenshot of postbank.apk during dynamic analysis (Source: Hatching Triage Sandbox )
Figure 8: Screenshot of postbank.apk during dynamic analysis (Source: Hatching Triage Sandbox )The C2 is hosted on Cloudflare London at the Yusuf Kemal TURKMENOGLU ASN.
 Figure 9: IP Overview for C2 in Hunt
Figure 9: IP Overview for C2 in HuntIn late May 2024, a web page hosted on port 80 of the C2 contained the defacement message "HACKED BY PersoDev." This page included a JavaScript script that turned off the right-click context menu and displayed an alert message. Additionally, it featured CSS to alter the opacity of images with a hover effect.
We don’t believe the two are related, but it is an interesting finding.
 Figure 10: Screenshot of ports and protocols for the associated IP in Hunt. Try it out!
Figure 10: Screenshot of ports and protocols for the associated IP in Hunt. Try it out!Directory Details
Open Directory & C2 IP: 5.252.74.45_443
postbank.apk SHA-1 hash: dc9a821f1e061098188503dbf7518bf263334fcd
C2 domain: oebonur600.duckdns_org
Triage Link: https://tria.ge/240617-mhv8yawgqb
Impacts on Users and Devices
The discovery of SpyNote samples in open directories poses significant risks to users, as these malicious files utilize additional infrastructure, including dynamic domains, for data exfiltration.
Once infected, users' sensitive information can be continuously siphoned to ever-changing locations, making detection and mitigation more challenging.
Conclusion
The SpyNote samples we've discussed show how even everyday apps like Google Translate and Temp Mail can be repurposed for malicious intent. These examples are just a handful of the over 40 SpyNote APKs available in Hunt, with many more likely operating undetected and stealing sensitive information.
To stay ahead of these threats, apply for a free demo of Hunt. Track and analyze numerous threats identified in open directories, analyze the infrastructure of over 80 malware families, and effectively protect your digital environment.
Related Posts:
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.