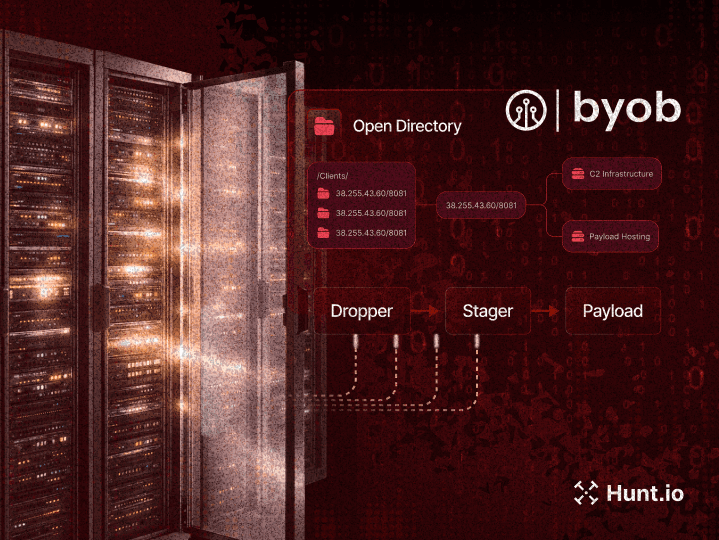
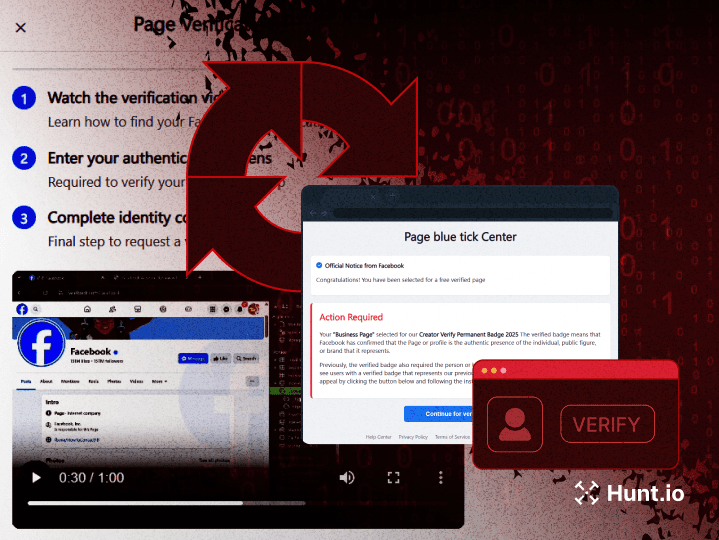
Malware Families
Malware Families
Explore an extensive collection of the most popular malware families, including detailed descriptions, tactics, and insights into their connections with threat actors. This page serves as a comprehensive resource for security professionals and researchers, offering valuable information to understand, detect, and defend against malware threats.
Explore an extensive collection of the most popular malware families, including detailed descriptions, tactics, and insights into their connections with threat actors. This page serves as a comprehensive resource for security professionals and researchers, offering valuable information to understand, detect, and defend against malware threats.
Search...
Search...
Top 10 Malware Families
Top 10 Malware Families
Malware Families FAQ
What are malware families and why do we need to know them to combat ever-changing threats?
What are malware families and why do we need to know them to combat ever-changing threats?
What are malware families and why do we need to know them to combat ever-changing threats?
How does malware affect businesses and what can we do to stop it?
How does malware affect businesses and what can we do to stop it?
How does malware affect businesses and what can we do to stop it?
How do attackers get into sensitive systems through malware?
How do attackers get into sensitive systems through malware?
How do attackers get into sensitive systems through malware?
How do organizations protect their operating systems from malware?
How do organizations protect their operating systems from malware?
How do organizations protect their operating systems from malware?
How do malicious files spread malware across the network?
How do malicious files spread malware across the network?
How do malicious files spread malware across the network?
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.