Threat Hunting Blog
Threat Hunting Blog
Check out our latest threat hunting articles, tips and stories
Check out our latest threat hunting articles, tips and stories
Check out our latest threat hunting articles, tips and stories
Product Updates
Latest Articles
Type
Victim Region
Malware
Attack Technique
Release Date

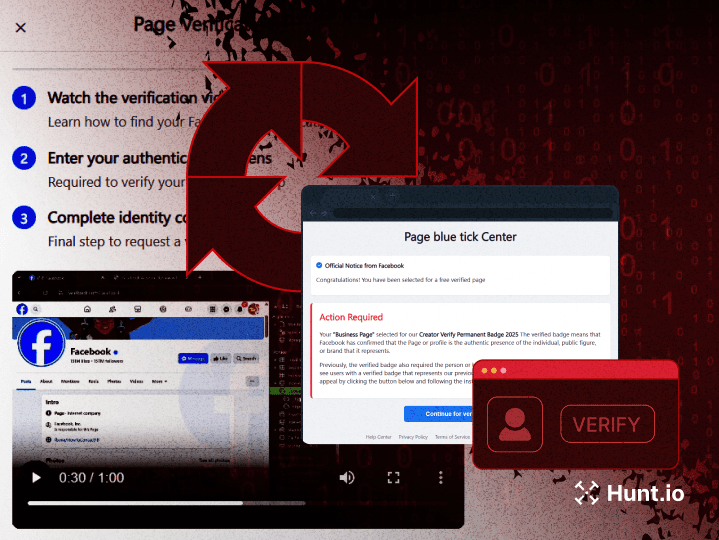
Shared SSH Keys Expose Coordinated Phishing Campaign Targeting Kuwaiti Fisheries and Telecom Sectors
Shared SSH keys expose coordinated phishing targeting Kuwaiti fisheries, telecoms, and insurers with cloned login portals and mobile payment lures. Learn more.
Threat Research
🌍 Middle East
Phishing & Social Engineering

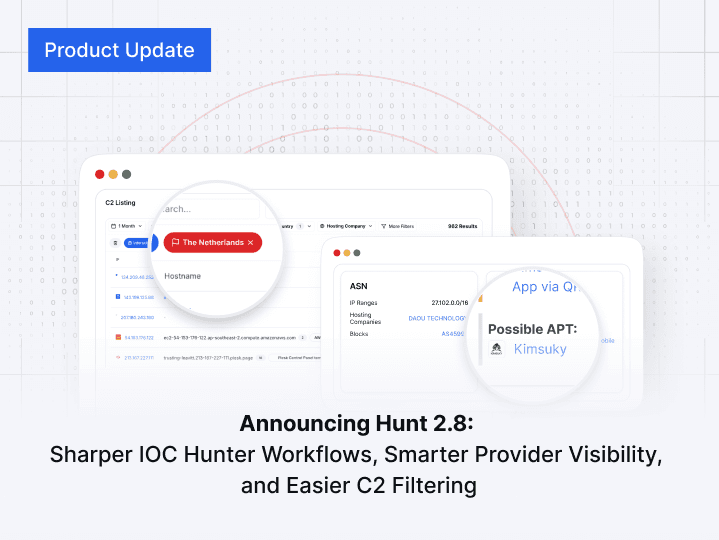
Advanced Threat Hunting with New SSL Features: Unlocking HuntSQL™ Anomaly Flags for Deeper Detection
Hunt.io enhances SSL threat hunting with new anomaly flags in HuntSQL™, improving the detection of misconfigurations, expired certificates, and malware infrastructure.
Product News

Learn how the 'Million OK!!!' HTTP response previously linked to Kimsuky has reappeared on new IPs and domains. This update provides the latest insights into evolving infrastructure, helping defenders stay informed on potential North Korean threat activity.
Threat Research
🇰🇷 South Korea
Beacon Reuse
Kimsuky

Uncovering Threat Actor Tactics: How Open Directories Provide Insight into XWorm Delivery Strategies
Learn how threat actors leverage open directories to deliver XWorm malware disguised as popular software, providing insight into their tactics.
Threat Research
🌍 Global
XWorm
Malware Delivery

Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Threat Research

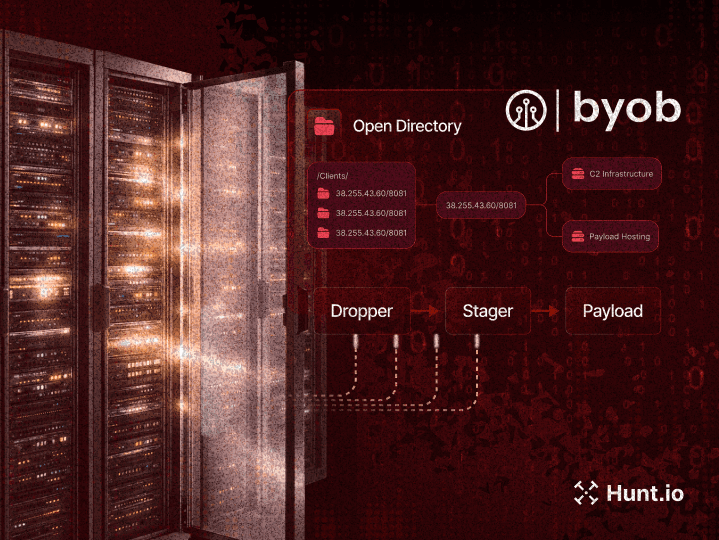
We originally launched our "Open Directory" feature in Hunt a year ago. The premise behind it was to get into the mind of the attacker by get a backstage view into their attacks. What we learned was that there was a ton of information that could be correlated and indexed. Today, we're reaffirming our commitment to getting into the tooling of attackers by launching AttackCapture™ by Hunt.io.
Product News

Following Recorded Future's (RF) report, "Exploring the Depths of SolarMarker's Multi-tiered Infrastructure," the Hunt Research Team leveraged the IOCs provided to discover a method of identifying clusters of SolarMarker servers in the wild.
Threat Research
🌎 North America
🇪🇺 Europe
SolarMarker
Malware Delivery
Multi-Stage Infection

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
Threat Research
Yakit

The Hunt Research Team vigilantly monitors GitHub, sifts through the IOC sections of threat intelligence reports, and scours various online forums for emerging threats, ensuring our detections stay practical and current for our customers. Our focus frequently turns to lesser-known threats that can still wreak havoc on the networks of uninformed defenders.
Threat Research
SparkRAT
Lateral Movement & Persistence

Shared SSH Keys Expose Coordinated Phishing Campaign Targeting Kuwaiti Fisheries and Telecom Sectors
Shared SSH keys expose coordinated phishing targeting Kuwaiti fisheries, telecoms, and insurers with cloned login portals and mobile payment lures. Learn more.
Threat Research
🌍 Middle East
Phishing & Social Engineering
May 2025

Advanced Threat Hunting with New SSL Features: Unlocking HuntSQL™ Anomaly Flags for Deeper Detection
Hunt.io enhances SSL threat hunting with new anomaly flags in HuntSQL™, improving the detection of misconfigurations, expired certificates, and malware infrastructure.
Product News
Feb 2025

Learn how the 'Million OK!!!' HTTP response previously linked to Kimsuky has reappeared on new IPs and domains. This update provides the latest insights into evolving infrastructure, helping defenders stay informed on potential North Korean threat activity.
Threat Research
🇰🇷 South Korea
Beacon Reuse
Kimsuky
Dec 2024

Uncovering Threat Actor Tactics: How Open Directories Provide Insight into XWorm Delivery Strategies
Learn how threat actors leverage open directories to deliver XWorm malware disguised as popular software, providing insight into their tactics.
Threat Research
🌍 Global
XWorm
Malware Delivery
Nov 2024

Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Threat Research
Oct 2024

We originally launched our "Open Directory" feature in Hunt a year ago. The premise behind it was to get into the mind of the attacker by get a backstage view into their attacks. What we learned was that there was a ton of information that could be correlated and indexed. Today, we're reaffirming our commitment to getting into the tooling of attackers by launching AttackCapture™ by Hunt.io.
Product News
Aug 2024

Following Recorded Future's (RF) report, "Exploring the Depths of SolarMarker's Multi-tiered Infrastructure," the Hunt Research Team leveraged the IOCs provided to discover a method of identifying clusters of SolarMarker servers in the wild.
Threat Research
🌎 North America
🇪🇺 Europe
SolarMarker
Malware Delivery
Multi-Stage Infection
May 2024

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
Threat Research
Yakit
May 2024

The Hunt Research Team vigilantly monitors GitHub, sifts through the IOC sections of threat intelligence reports, and scours various online forums for emerging threats, ensuring our detections stay practical and current for our customers. Our focus frequently turns to lesser-known threats that can still wreak havoc on the networks of uninformed defenders.
Threat Research
SparkRAT
Lateral Movement & Persistence
Apr 2024

Shared SSH Keys Expose Coordinated Phishing Campaign Targeting Kuwaiti Fisheries and Telecom Sectors
Shared SSH keys expose coordinated phishing targeting Kuwaiti fisheries, telecoms, and insurers with cloned login portals and mobile payment lures. Learn more.
Threat Research
🌍 Middle East
Phishing & Social Engineering
May 2025

Advanced Threat Hunting with New SSL Features: Unlocking HuntSQL™ Anomaly Flags for Deeper Detection
Hunt.io enhances SSL threat hunting with new anomaly flags in HuntSQL™, improving the detection of misconfigurations, expired certificates, and malware infrastructure.
Product News
Feb 2025

Learn how the 'Million OK!!!' HTTP response previously linked to Kimsuky has reappeared on new IPs and domains. This update provides the latest insights into evolving infrastructure, helping defenders stay informed on potential North Korean threat activity.
Threat Research
🇰🇷 South Korea
Beacon Reuse
Kimsuky
Dec 2024

Uncovering Threat Actor Tactics: How Open Directories Provide Insight into XWorm Delivery Strategies
Learn how threat actors leverage open directories to deliver XWorm malware disguised as popular software, providing insight into their tactics.
Threat Research
🌍 Global
XWorm
Malware Delivery
Nov 2024

Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Threat Research
Oct 2024

We originally launched our "Open Directory" feature in Hunt a year ago. The premise behind it was to get into the mind of the attacker by get a backstage view into their attacks. What we learned was that there was a ton of information that could be correlated and indexed. Today, we're reaffirming our commitment to getting into the tooling of attackers by launching AttackCapture™ by Hunt.io.
Product News
Aug 2024

Following Recorded Future's (RF) report, "Exploring the Depths of SolarMarker's Multi-tiered Infrastructure," the Hunt Research Team leveraged the IOCs provided to discover a method of identifying clusters of SolarMarker servers in the wild.
Threat Research
🌎 North America
🇪🇺 Europe
SolarMarker
Malware Delivery
Multi-Stage Infection
May 2024

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
Threat Research
Yakit
May 2024

The Hunt Research Team vigilantly monitors GitHub, sifts through the IOC sections of threat intelligence reports, and scours various online forums for emerging threats, ensuring our detections stay practical and current for our customers. Our focus frequently turns to lesser-known threats that can still wreak havoc on the networks of uninformed defenders.
Threat Research
SparkRAT
Lateral Movement & Persistence
Apr 2024

Shared SSH Keys Expose Coordinated Phishing Campaign Targeting Kuwaiti Fisheries and Telecom Sectors
Shared SSH keys expose coordinated phishing targeting Kuwaiti fisheries, telecoms, and insurers with cloned login portals and mobile payment lures. Learn more.
Threat Research
🌍 Middle East
Phishing & Social Engineering
May 2025

Advanced Threat Hunting with New SSL Features: Unlocking HuntSQL™ Anomaly Flags for Deeper Detection
Hunt.io enhances SSL threat hunting with new anomaly flags in HuntSQL™, improving the detection of misconfigurations, expired certificates, and malware infrastructure.
Product News
Feb 2025

Learn how the 'Million OK!!!' HTTP response previously linked to Kimsuky has reappeared on new IPs and domains. This update provides the latest insights into evolving infrastructure, helping defenders stay informed on potential North Korean threat activity.
Threat Research
🇰🇷 South Korea
Beacon Reuse
Kimsuky
Dec 2024

Uncovering Threat Actor Tactics: How Open Directories Provide Insight into XWorm Delivery Strategies
Learn how threat actors leverage open directories to deliver XWorm malware disguised as popular software, providing insight into their tactics.
Threat Research
🌍 Global
XWorm
Malware Delivery
Nov 2024

Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Threat Research
Oct 2024

We originally launched our "Open Directory" feature in Hunt a year ago. The premise behind it was to get into the mind of the attacker by get a backstage view into their attacks. What we learned was that there was a ton of information that could be correlated and indexed. Today, we're reaffirming our commitment to getting into the tooling of attackers by launching AttackCapture™ by Hunt.io.
Product News
Aug 2024

Following Recorded Future's (RF) report, "Exploring the Depths of SolarMarker's Multi-tiered Infrastructure," the Hunt Research Team leveraged the IOCs provided to discover a method of identifying clusters of SolarMarker servers in the wild.
Threat Research
🌎 North America
🇪🇺 Europe
SolarMarker
Malware Delivery
Multi-Stage Infection
May 2024

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
Threat Research
Yakit
May 2024

The Hunt Research Team vigilantly monitors GitHub, sifts through the IOC sections of threat intelligence reports, and scours various online forums for emerging threats, ensuring our detections stay practical and current for our customers. Our focus frequently turns to lesser-known threats that can still wreak havoc on the networks of uninformed defenders.
Threat Research
SparkRAT
Lateral Movement & Persistence
Apr 2024
Ready to See Hunt.io in Action?
Ready to See Hunt.io in Action?
Ready to See Hunt.io in Action?
Explore how our platform helps you find real threats, not noise.
Explore how our platform helps you find real threats, not noise.
Explore how our platform helps you find real threats, not noise.



Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.