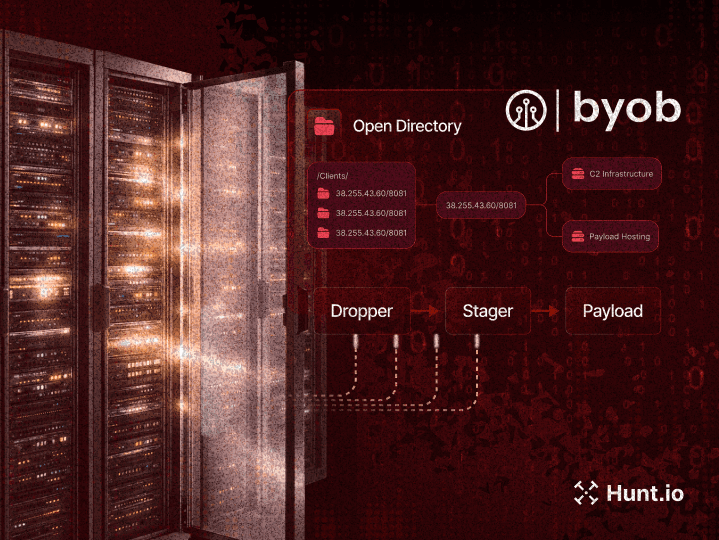
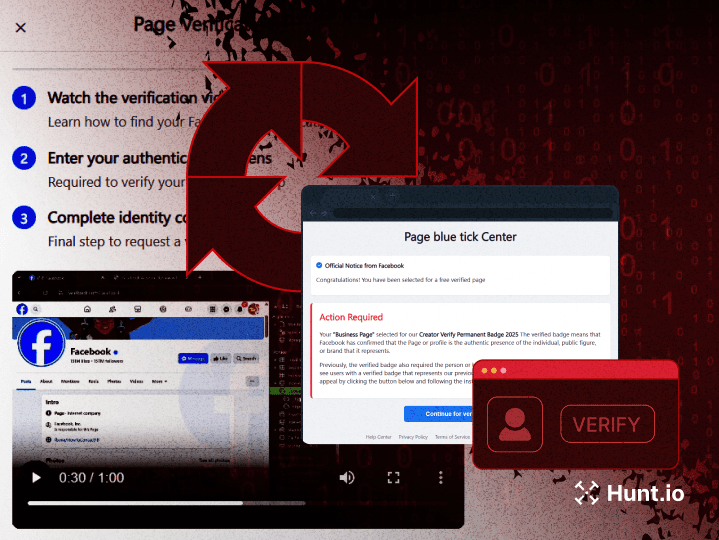
Threat Hunting Glossary
Threat Hunting Glossary
Discover our comprehensive Threat Hunting Glossary, your go-to guide for mastering Threat Hunting 101. This glossary covers a wide range of essential terms and definitions every cybersecurity professional should know. Get detailed explanations of C2 servers, malicious infrastructure, open directories, malware, threat actors, different types of attacks, and much more. Whether you're new to threat hunting or looking to sharpen your skills, our glossary provides the foundational knowledge needed to identify and mitigate cyber threats effectively.
Discover our comprehensive Threat Hunting Glossary, your go-to guide for mastering Threat Hunting 101. This glossary covers a wide range of essential terms and definitions every cybersecurity professional should know. Get detailed explanations of C2 servers, malicious infrastructure, open directories, malware, threat actors, different types of attacks, and much more. Whether you're new to threat hunting or looking to sharpen your skills, our glossary provides the foundational knowledge needed to identify and mitigate cyber threats effectively.
Previous
of
Next
of
Next
of
Next
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.