Linux Threat Hunting: Techniques and Tools Explained
Published on
Published on
Published on
Jan 22, 2026
Jan 22, 2026
Jan 22, 2026



Linux threat hunting has become a core discipline for security teams running modern infrastructure. Linux now powers the majority of cloud platforms, production web servers, CI/CD pipelines, and internal tooling, holding 63.1% of the global server market. That dominance also makes it a prime target for attackers looking to gain access, persist quietly, and move laterally across networks.
The impact of a successful compromise can be severe, with the average cost of a security incident reaching USD 4.88 million this year. As a result, proactive threat hunting on Linux systems is no longer optional.
In this guide, we take a practical approach to Linux threat hunting, breaking down how attackers steal credentials, maintain persistence, escalate privileges, and stay hidden in real-world environments.
Introduction to Threat Hunting in Linux

We all know Linux. This is the operating system that "runs most of the Internet, all of the world's top 500 supercomputers, and the world's stock exchanges," as stated by Linux.com, and that level of adoption makes it a high-value target for attackers.
Threat hunting is a proactive practice. Instead of waiting for alerts, teams actively hunt for indicators of compromise (IOCs) across the operating system, logs, memory, and running processes. In Linux, this often means digging into areas attackers rely on for initial access, persistence, and long-term access.
Effective Linux threat hunting blends open source tools, built-in capabilities, and strong operational knowledge. Tools like Auditd, Osquery, Sysmon for Linux, and other security tools help responders understand the current state of the system and spot deviations from normal behavior.
This approach strengthens the overall security posture, especially when combined with data from threat intelligence feeds and continuous monitoring.
With that foundation in place, the next step is understanding how attackers first deepen their access. In most Linux intrusions, this starts with credential theft.
Credential Access in Linux Systems
Credential access is usually the first real objective once an attacker gets a foothold. Linux systems often store credentials in configuration files, environment settings, scripts, or memory. If attackers can harvest credentials, they can escalate privileges, pivot to other systems, or access sensitive services.
Detecting credential access early is critical to protecting sensitive data and preventing a wider Linux threat from spreading.
Memory Dumps and Password Files Search
One of the most effective techniques during incident response is analyzing memory dumps and performing a password file search. Memory can reveal cleartext passwords, tokens, or traces of malicious code that never touched the disk.
Using commands like strings, combined with grep across memory dumps and log data, helps uncover credentials used by attackers. These techniques also support further investigation when reconstructing how access was gained.
Public Key and SSH Key Detection
SSH-based access is extremely common in Linux environments. Attackers often drop new ssh key entries or reuse stolen private keys to maintain persistence.
Regular audits of authorized keys, including checks for unknown public key entries tied to a user account, are essential. Any unexpected SSH key on a Linux server should be treated as suspicious until proven otherwise.
Once credentials are obtained, attackers rarely stop there. Their next priority is to ensure continued access, even if passwords are changed or systems are rebooted.

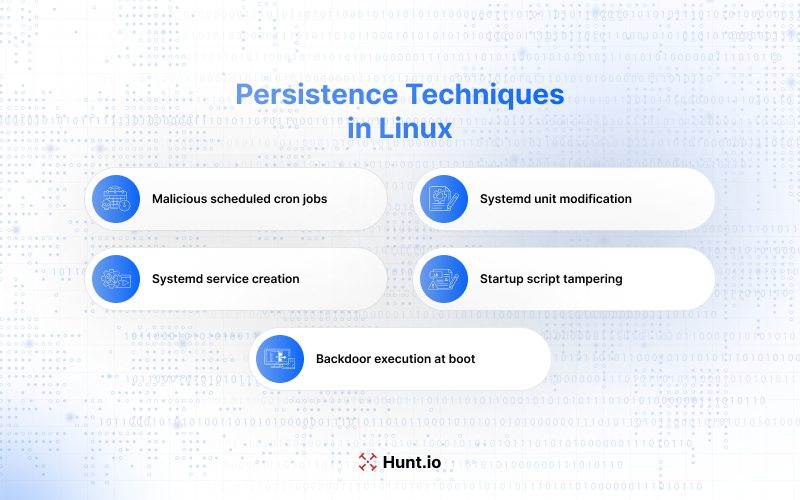
Persistence Techniques in Linux
Persistence is what allows attackers to survive reboots, updates, and partial remediation. A well-placed persistence technique lets them quietly regain access whenever needed.
Linux offers many persistence paths, from cron jobs to system services to login scripts.
Crontab Jobs and Malicious Scripts
Cron jobs remain one of the most abused persistence methods. Attackers use them to schedule malicious scripts, deploy backdoors, or launch a reverse shell on a timer.
Hunting for unknown cron entries and suspicious files referenced by those jobs is a must. This is especially important on production Linux servers and shared virtual machines.
Systemd Service Manipulation
Systemd is deeply integrated into the Linux system, which makes it attractive for attackers seeking persistence with root permission.
A malicious systemd unit can run commands at startup, beacon to a command and control (C2) endpoint, or spawn a reverse shell repeatedly. Checking /etc/systemd/system for unauthorized services is a common and effective hunting technique.
Systemd abuse is often paired with other techniques to avoid detection, especially during post-exploitation activities.
While persistence mechanisms often target the operating system directly, web-facing Linux servers introduce a different attack surface: one where access can be maintained through application-level backdoors.
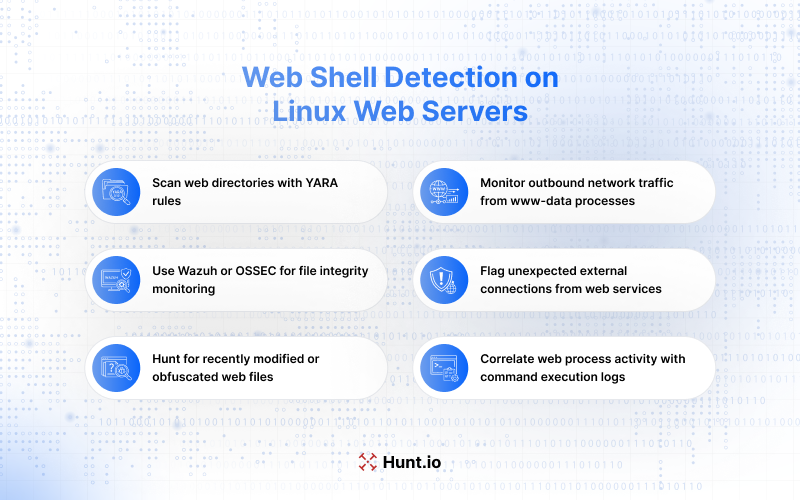
Web Shell Detection on Linux Web Servers
A web shell is a lightweight backdoor planted on a compromised web server. It allows attackers to execute commands remotely using HTTP requests.
YARA rules, Wazuh, OSSEC, and custom forensic scanners are frequently used to detect web shells embedded within legitimate application files. In parallel, monitoring outbound network activity from processes running as www-data can reveal command-and-control traffic or data exfiltration attempts.
Any unexpected outbound connection from a web process could indicate a reverse shell or data staging for data exfiltration.
Web shells often provide attackers with an initial execution foothold, but limited privileges can restrict their impact. To gain full control of the system, attackers typically move quickly toward privilege escalation.
Privilege Escalation and Logging in Linux
Once attackers gain a foothold, privilege escalation is usually next. Elevated privileges unlock full control over the Linux system and enable deeper compromise.
Abusing Setuid and Setgid Files
Misconfigured setuid and setgid binaries are classic escalation paths. Attackers replace or abuse these files to run commands with elevated privileges.
Hunting for unusual permission changes, ownership anomalies, and recently modified binaries helps detect this behavior.
Modifying /etc/sudoers
Another common tactic is modifying /etc/sudoers to grant elevated execution rights. Attackers may hide their changes or blend them with legitimate entries to reduce suspicion.
Auditing sudoers regularly is a simple but effective defense against privilege escalation.
File and Directory Permission Changes
Attackers often change file permissions or ACLs using tools like setfacl. Tracking unauthorized permission changes helps uncover stealthy escalation paths.
Logging and Visibility
Strong Linux logging is essential for effective threat hunting and incident response. Logs provide context around user actions, command execution, file access, and network behavior.
Tools like syslog, auditd, and Auditbeat allow responders to track activity across the operating system. Combined with a SIEM, these logs help correlate events and surface patterns tied to advanced threats.
When logs and telemetry reveal clear signs of compromise, the focus shifts from detection to response. At this stage, speed and structure are critical to limiting damage.
Incident Response and Analysis
When a Linux threat is confirmed, structured incident response becomes critical. This includes live response, volatile data collection, and disk analysis.
Live Response and Volatile Data Collection
Live response focuses on capturing volatile memory, running processes, open network connections, and loaded modules. Tools like Velociraptor and OSSEC enable fast data capture with minimal system impact.
This data often contains key clues about attacker access, tooling, and command execution.
Disk Analysis and Evidence Collection
Disk analysis helps reconstruct the attack timeline and identify persistence artifacts. Building timelines gives responders a better understanding of attacker behavior and decision points.
A dedicated forensic tool like The Sleuth Kit can help extract technical artifacts while preserving evidence integrity.
While basic response actions address immediate threats, advanced attackers often leave behind subtle traces that require deeper analysis to uncover.
Advanced Linux Threat Hunting Techniques
Advanced threat hunting in Linux goes beyond basic checks. Techniques like timeline generation and detection of anti-forensic behavior help uncover hidden activity.
Timeline Correlation Across Subsystems
Timelines are most powerful when built across multiple data sources. File metadata, shell history, authentication logs, and network telemetry often reveal patterns that single sources miss.
Correlating these timelines exposes gaps, overlaps, and execution chains that point to manual attacker activity.
Detecting Living-off-the-Land Abuse
Attackers increasingly rely on native binaries like curl, wget, bash, python, and systemctl to avoid detection.
Threat hunters should track unusual execution contexts, such as network tools spawned from cron jobs or scripting engines launched by web processes.
Identifying Anti-Forensic Behavior
Advanced actors manipulate timestamps, clear logs, and unset environment variables to hide activity. Inconsistencies between filesystem metadata, process history, and network logs often expose tampering.
Infrastructure-Aware Hunting
Host-level data alone rarely tells the full story. Mapping outbound connections to known malicious infrastructure often reveals compromised Linux hosts that appear clean internally.
This is where infrastructure intelligence becomes a force multiplier.
Enter Hunt.io
At Hunt, we give threat hunters the visibility and tools to uncover malicious activity that often targets Linux infrastructure. Our platform continuously tracks and validates active command-and-control (C2) servers and malicious infrastructure at Internet scale, letting us spot suspicious servers and domains that may interact with compromised Linux hosts.
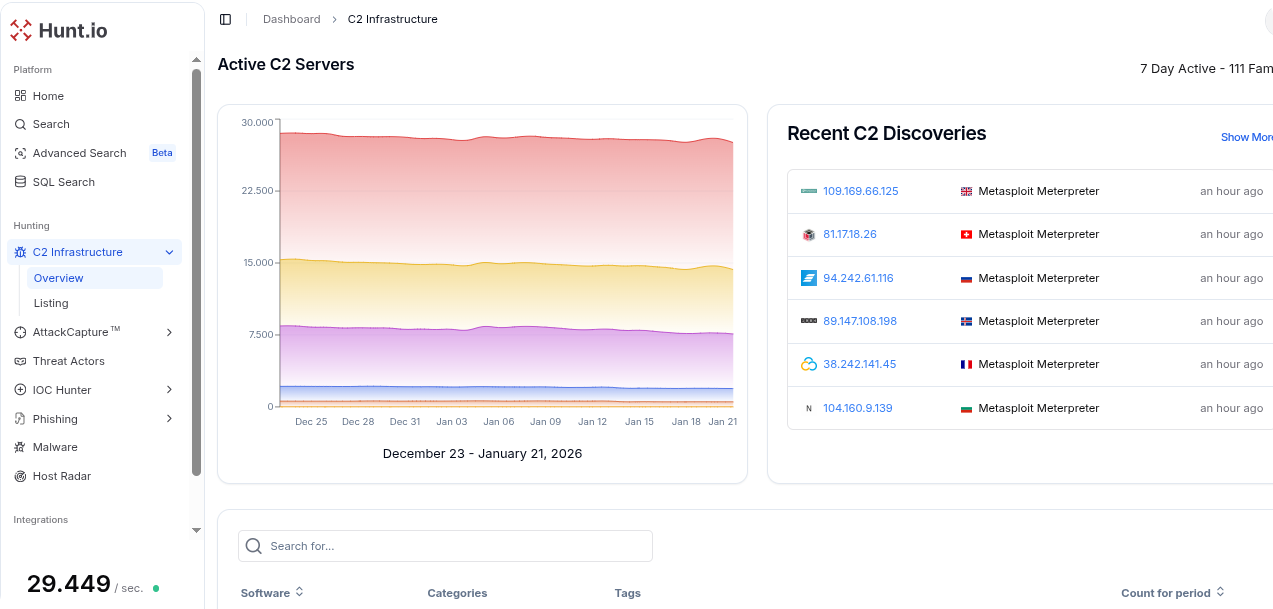
With features like AttackCapture™ and IOC Hunter, we automatically surface exploit artifacts, open directories, and indicators of compromise to accelerate investigations.
HuntSQL™ lets us query and analyze vast datasets to identify anomalous patterns, while enriched feeds help correlate Linux-specific behaviors with known adversary infrastructure. Together, these tools empower us to hunt threats across Linux environments with confidence and precision.
Our advanced threat hunting platform shows its capabilities when applied to real investigations. The following examples show how Linux threat hunting and infrastructure analysis come together in practice.
Ejemplo de detecciojn de web shells como c99, aca https://app.hunt.io/file-manager?host=http://105.73.33.126:8001
Real-World Examples
Let's see a couple of hands-on examples to reinforce why Linux threat hunting matters.
APT36-Style ClickFix Attack Spoofs Indian Ministry to Target Windows & Linux: During this investigation, we found how ClickFix-style social engineering was being adapted for Linux users through spoofed government infrastructure. A cloned Indian Ministry of Defence press portal selectively delivered a Linux-specific flow that relied on clipboard-based shell command execution rather than direct exploitation.

Victims were guided to paste and run a downloaded shell script hosted on a likely compromised domain, masked behind fake CAPTCHA prompts and trusted visual cues. Although the Linux payload observed was currently non-functional, the delivery mechanism highlights growing interest in cross-platform targeting and low-friction execution techniques against Linux environments.
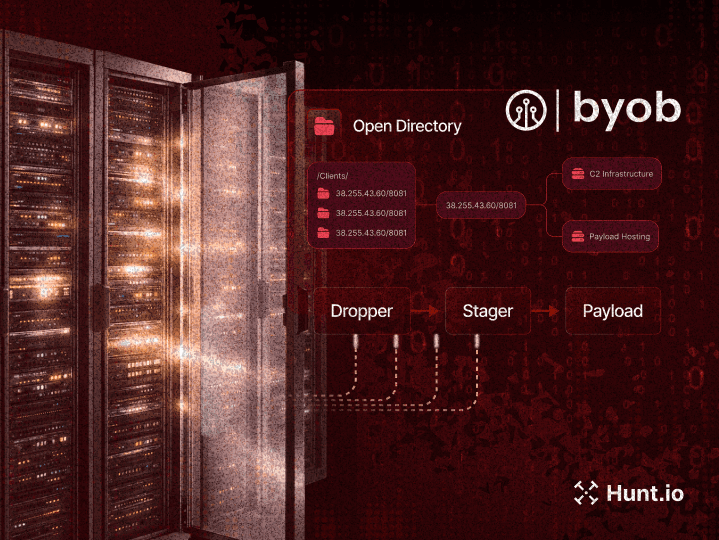
Geacon and Geacon_Pro: A Constant Menace to Linux and Windows Systems: Our research highlighted the growing use of Golang-based Cobalt Strike variants, such as Geacon and Geacon_Pro, to target Linux environments alongside Windows. Multiple servers were found hosting Linux ELF payloads, bash scripts, and persistence mechanisms that masquerade as legitimate services like Zabbix.
Open directories exposed Linux-focused tooling, including systemd service abuse, reverse proxy binaries, and Golang implants communicating with Cloudflare-backed C2 infrastructure. Our findings show how modern offensive frameworks increasingly treat Linux as a first-class target, reinforcing the need for Linux-specific threat hunting strategies.
Conclusion
Linux threat hunting is essential for detecting modern attacks targeting servers and cloud workloads. From credential theft to persistence and C2 infrastructure, visibility matters. Ready to see how we help security teams uncover malicious Linux activity at scale? Book a demo now to see our platform in action.
Linux threat hunting has become a core discipline for security teams running modern infrastructure. Linux now powers the majority of cloud platforms, production web servers, CI/CD pipelines, and internal tooling, holding 63.1% of the global server market. That dominance also makes it a prime target for attackers looking to gain access, persist quietly, and move laterally across networks.
The impact of a successful compromise can be severe, with the average cost of a security incident reaching USD 4.88 million this year. As a result, proactive threat hunting on Linux systems is no longer optional.
In this guide, we take a practical approach to Linux threat hunting, breaking down how attackers steal credentials, maintain persistence, escalate privileges, and stay hidden in real-world environments.
Introduction to Threat Hunting in Linux

We all know Linux. This is the operating system that "runs most of the Internet, all of the world's top 500 supercomputers, and the world's stock exchanges," as stated by Linux.com, and that level of adoption makes it a high-value target for attackers.
Threat hunting is a proactive practice. Instead of waiting for alerts, teams actively hunt for indicators of compromise (IOCs) across the operating system, logs, memory, and running processes. In Linux, this often means digging into areas attackers rely on for initial access, persistence, and long-term access.
Effective Linux threat hunting blends open source tools, built-in capabilities, and strong operational knowledge. Tools like Auditd, Osquery, Sysmon for Linux, and other security tools help responders understand the current state of the system and spot deviations from normal behavior.
This approach strengthens the overall security posture, especially when combined with data from threat intelligence feeds and continuous monitoring.
With that foundation in place, the next step is understanding how attackers first deepen their access. In most Linux intrusions, this starts with credential theft.
Credential Access in Linux Systems
Credential access is usually the first real objective once an attacker gets a foothold. Linux systems often store credentials in configuration files, environment settings, scripts, or memory. If attackers can harvest credentials, they can escalate privileges, pivot to other systems, or access sensitive services.
Detecting credential access early is critical to protecting sensitive data and preventing a wider Linux threat from spreading.
Memory Dumps and Password Files Search
One of the most effective techniques during incident response is analyzing memory dumps and performing a password file search. Memory can reveal cleartext passwords, tokens, or traces of malicious code that never touched the disk.
Using commands like strings, combined with grep across memory dumps and log data, helps uncover credentials used by attackers. These techniques also support further investigation when reconstructing how access was gained.
Public Key and SSH Key Detection
SSH-based access is extremely common in Linux environments. Attackers often drop new ssh key entries or reuse stolen private keys to maintain persistence.
Regular audits of authorized keys, including checks for unknown public key entries tied to a user account, are essential. Any unexpected SSH key on a Linux server should be treated as suspicious until proven otherwise.
Once credentials are obtained, attackers rarely stop there. Their next priority is to ensure continued access, even if passwords are changed or systems are rebooted.

Persistence Techniques in Linux
Persistence is what allows attackers to survive reboots, updates, and partial remediation. A well-placed persistence technique lets them quietly regain access whenever needed.
Linux offers many persistence paths, from cron jobs to system services to login scripts.
Crontab Jobs and Malicious Scripts
Cron jobs remain one of the most abused persistence methods. Attackers use them to schedule malicious scripts, deploy backdoors, or launch a reverse shell on a timer.
Hunting for unknown cron entries and suspicious files referenced by those jobs is a must. This is especially important on production Linux servers and shared virtual machines.
Systemd Service Manipulation
Systemd is deeply integrated into the Linux system, which makes it attractive for attackers seeking persistence with root permission.
A malicious systemd unit can run commands at startup, beacon to a command and control (C2) endpoint, or spawn a reverse shell repeatedly. Checking /etc/systemd/system for unauthorized services is a common and effective hunting technique.
Systemd abuse is often paired with other techniques to avoid detection, especially during post-exploitation activities.
While persistence mechanisms often target the operating system directly, web-facing Linux servers introduce a different attack surface: one where access can be maintained through application-level backdoors.

Web Shell Detection on Linux Web Servers
A web shell is a lightweight backdoor planted on a compromised web server. It allows attackers to execute commands remotely using HTTP requests.
YARA rules, Wazuh, OSSEC, and custom forensic scanners are frequently used to detect web shells embedded within legitimate application files. In parallel, monitoring outbound network activity from processes running as www-data can reveal command-and-control traffic or data exfiltration attempts.
Any unexpected outbound connection from a web process could indicate a reverse shell or data staging for data exfiltration.
Web shells often provide attackers with an initial execution foothold, but limited privileges can restrict their impact. To gain full control of the system, attackers typically move quickly toward privilege escalation.
Privilege Escalation and Logging in Linux
Once attackers gain a foothold, privilege escalation is usually next. Elevated privileges unlock full control over the Linux system and enable deeper compromise.
Abusing Setuid and Setgid Files
Misconfigured setuid and setgid binaries are classic escalation paths. Attackers replace or abuse these files to run commands with elevated privileges.
Hunting for unusual permission changes, ownership anomalies, and recently modified binaries helps detect this behavior.
Modifying /etc/sudoers
Another common tactic is modifying /etc/sudoers to grant elevated execution rights. Attackers may hide their changes or blend them with legitimate entries to reduce suspicion.
Auditing sudoers regularly is a simple but effective defense against privilege escalation.
File and Directory Permission Changes
Attackers often change file permissions or ACLs using tools like setfacl. Tracking unauthorized permission changes helps uncover stealthy escalation paths.
Logging and Visibility
Strong Linux logging is essential for effective threat hunting and incident response. Logs provide context around user actions, command execution, file access, and network behavior.
Tools like syslog, auditd, and Auditbeat allow responders to track activity across the operating system. Combined with a SIEM, these logs help correlate events and surface patterns tied to advanced threats.
When logs and telemetry reveal clear signs of compromise, the focus shifts from detection to response. At this stage, speed and structure are critical to limiting damage.
Incident Response and Analysis
When a Linux threat is confirmed, structured incident response becomes critical. This includes live response, volatile data collection, and disk analysis.
Live Response and Volatile Data Collection
Live response focuses on capturing volatile memory, running processes, open network connections, and loaded modules. Tools like Velociraptor and OSSEC enable fast data capture with minimal system impact.
This data often contains key clues about attacker access, tooling, and command execution.
Disk Analysis and Evidence Collection
Disk analysis helps reconstruct the attack timeline and identify persistence artifacts. Building timelines gives responders a better understanding of attacker behavior and decision points.
A dedicated forensic tool like The Sleuth Kit can help extract technical artifacts while preserving evidence integrity.
While basic response actions address immediate threats, advanced attackers often leave behind subtle traces that require deeper analysis to uncover.

Advanced Linux Threat Hunting Techniques
Advanced threat hunting in Linux goes beyond basic checks. Techniques like timeline generation and detection of anti-forensic behavior help uncover hidden activity.
Timeline Correlation Across Subsystems
Timelines are most powerful when built across multiple data sources. File metadata, shell history, authentication logs, and network telemetry often reveal patterns that single sources miss.
Correlating these timelines exposes gaps, overlaps, and execution chains that point to manual attacker activity.
Detecting Living-off-the-Land Abuse
Attackers increasingly rely on native binaries like curl, wget, bash, python, and systemctl to avoid detection.
Threat hunters should track unusual execution contexts, such as network tools spawned from cron jobs or scripting engines launched by web processes.
Identifying Anti-Forensic Behavior
Advanced actors manipulate timestamps, clear logs, and unset environment variables to hide activity. Inconsistencies between filesystem metadata, process history, and network logs often expose tampering.
Infrastructure-Aware Hunting
Host-level data alone rarely tells the full story. Mapping outbound connections to known malicious infrastructure often reveals compromised Linux hosts that appear clean internally.
This is where infrastructure intelligence becomes a force multiplier.
Enter Hunt.io
At Hunt, we give threat hunters the visibility and tools to uncover malicious activity that often targets Linux infrastructure. Our platform continuously tracks and validates active command-and-control (C2) servers and malicious infrastructure at Internet scale, letting us spot suspicious servers and domains that may interact with compromised Linux hosts.

With features like AttackCapture™ and IOC Hunter, we automatically surface exploit artifacts, open directories, and indicators of compromise to accelerate investigations.
HuntSQL™ lets us query and analyze vast datasets to identify anomalous patterns, while enriched feeds help correlate Linux-specific behaviors with known adversary infrastructure. Together, these tools empower us to hunt threats across Linux environments with confidence and precision.
Our advanced threat hunting platform shows its capabilities when applied to real investigations. The following examples show how Linux threat hunting and infrastructure analysis come together in practice.
Ejemplo de detecciojn de web shells como c99, aca https://app.hunt.io/file-manager?host=http://105.73.33.126:8001
Real-World Examples
Let's see a couple of hands-on examples to reinforce why Linux threat hunting matters.
APT36-Style ClickFix Attack Spoofs Indian Ministry to Target Windows & Linux: During this investigation, we found how ClickFix-style social engineering was being adapted for Linux users through spoofed government infrastructure. A cloned Indian Ministry of Defence press portal selectively delivered a Linux-specific flow that relied on clipboard-based shell command execution rather than direct exploitation.

Victims were guided to paste and run a downloaded shell script hosted on a likely compromised domain, masked behind fake CAPTCHA prompts and trusted visual cues. Although the Linux payload observed was currently non-functional, the delivery mechanism highlights growing interest in cross-platform targeting and low-friction execution techniques against Linux environments.
Geacon and Geacon_Pro: A Constant Menace to Linux and Windows Systems: Our research highlighted the growing use of Golang-based Cobalt Strike variants, such as Geacon and Geacon_Pro, to target Linux environments alongside Windows. Multiple servers were found hosting Linux ELF payloads, bash scripts, and persistence mechanisms that masquerade as legitimate services like Zabbix.

Open directories exposed Linux-focused tooling, including systemd service abuse, reverse proxy binaries, and Golang implants communicating with Cloudflare-backed C2 infrastructure. Our findings show how modern offensive frameworks increasingly treat Linux as a first-class target, reinforcing the need for Linux-specific threat hunting strategies.
Conclusion
Linux threat hunting is essential for detecting modern attacks targeting servers and cloud workloads. From credential theft to persistence and C2 infrastructure, visibility matters. Ready to see how we help security teams uncover malicious Linux activity at scale? Book a demo now to see our platform in action.
Related Posts:
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.