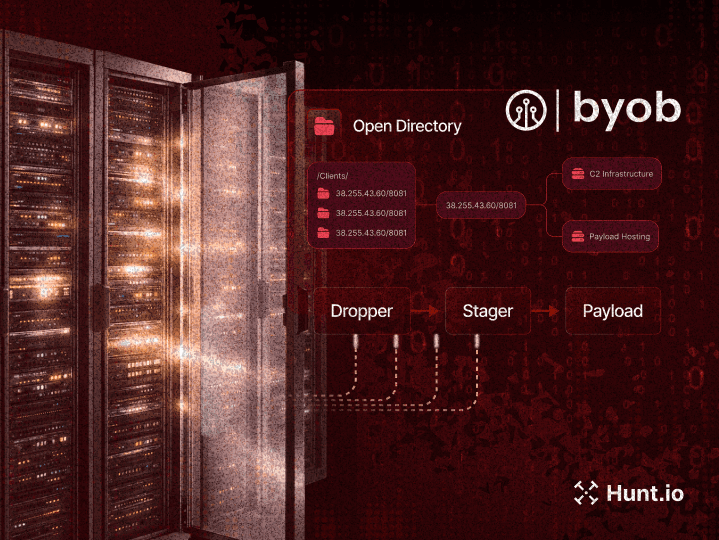
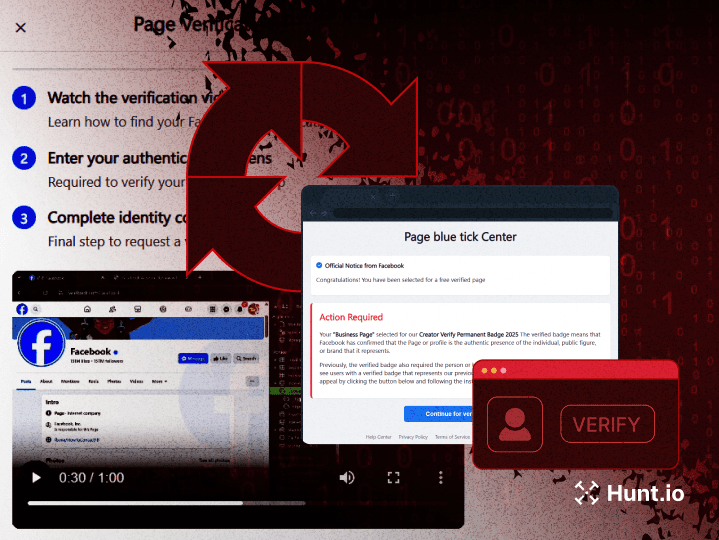
Built for OEMs
Detect Active Threat Actor Infrastructure at Scale
Detect Active Threat Actor Infrastructure at Scale
Power your platform with real-time feeds and enrichment APIs that help your customers uncover attacker behavior faster.
Power your platform with real-time feeds and enrichment APIs that help your customers uncover attacker behavior faster.
Why OEMs choose Hunt.io:
Why OEMs choose Hunt.io:
Real-time threat infrastructure feeds linked to active campaigns and actors
Real-time threat infrastructure feeds linked to active campaigns and actors
Real-time threat infrastructure feeds linked to active campaigns and actors
Enrichment APIs for IPs, domains, and hashes – with confidence scoring and attribution
Enrichment APIs for IPs, domains, and hashes – with confidence scoring and attribution
Enrichment APIs for IPs, domains, and hashes – with confidence scoring and attribution
Detection-ready data – not dashboards or passive telemetry
Detection-ready data – not dashboards or passive telemetry
Detection-ready data – not dashboards or passive telemetry
White-label support and OEM licensing with fast integration
White-label support and OEM licensing with fast integration
White-label support and OEM licensing with fast integration
MSSP-ready: scale threat detection without expanding your team
MSSP-ready: scale threat detection without expanding your team
MSSP-ready: scale threat detection without expanding your team
Built for Threat Detection Platforms
Built for Threat Detection Platforms

Correlate infrastructure tied to known threat actors inside your SIEM or XDR
Enrich IOCs from endpoint events to validate attacker presence
Auto-tag suspicious domains or IPs with actor attribution and infrastructure context
What You Get
What You Get
Access to real-time C2 infrastructure feeds & API with 95 %+ confidence
Access to real-time C2 infrastructure feeds & API with 95 %+ confidence
Access to real-time C2 infrastructure feeds & API with 95 %+ confidence
Enrichment endpoints for IPs, domains, and file hashes
Enrichment endpoints for IPs, domains, and file hashes
Enrichment endpoints for IPs, domains, and file hashes
Attribution data mapped to threat actors and known campaigns
Attribution data mapped to threat actors and known campaigns
Attribution data mapped to threat actors and known campaigns
Technical support, integration assistance, and documentation
Technical support, integration assistance, and documentation
Technical support, integration assistance, and documentation
Flexible licensing for OEM and MSSP models
Flexible licensing for OEM and MSSP models
Flexible licensing for OEM and MSSP models
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.