Widespread gov.br Subdomain Abuse: 630k+ URLs Leveraged for Black Hat SEO Redirects
Published on
Published on
Published on
Jul 17, 2025
Jul 17, 2025
Jul 17, 2025





While investigating threats targeting Brazil and the broader South American region, we came across a suspicious server hosted at IP 3x.xx.xx.xx. What initially caught our attention was the volume of templated HTML files and Python scripts, which were clearly designed for large-scale automation.
Digging deeper, I realized this infrastructure was actively generating fake government-style pages by hijacking subdomains under
.gov.br. These pages were being used in a massive black hat SEO campaign to manipulate search engine results and redirect users to deceptive sites.
Please note that we have chosen to redact certain indicators in coordination with the Brazilian CTIR, as their investigation into this attack is still ongoing.
Executive Summary
Multiple subdomains under the Brazilian government's .gov.br domain have been hijacked and are currently being exploited to host or redirect to malicious websites.
These compromised subdomains are being used in a large-scale SEO poisoning campaign, where unsuspecting users searching online are funneled toward fraudulent gambling, betting, or scam pages.
Using Hunt.io's AttackCapture™ capability, we traced the infrastructure behind this operation to a single server hosting the full stack of automation scripts, templated HTML, and keyword manipulation tools fueling the campaign.
In this report, we will discuss the techniques used to mislead Brazilian Internet users when performing searches to clear their queries.
Campaign Overview
While searching for threats targeting the Brazilian region, analysts discovered a widespread SEO poisoning campaign exploiting hijacked subdomains under
.gov.br.
The discovery was made on 27th June 2025 using Hunt.io's AttackCapture™ feature, which surfaced an exposed server 38.xx.xx.xx:xx hosted by Kaopu Cloud HK Limited.
The server contained automation scripts, keyword databases, and templated HTML content used to generate thousands of fake, search-optimized URLs.
These URLs are served via compromised government infrastructure and are designed to redirect users to malicious or deceptive content, including gambling, betting, and investment-themed landing pages.
Search Engine Poisoning
Search Engine Poisoning (SEP) is a technique used by threat actors to manipulate search engine algorithms, causing malicious or misleading websites to appear among the top search results.
By mimicking legitimate content and abusing high-authority domains, attackers can redirect users searching for trustworthy information to fraudulent or harmful websites, often without their knowledge.
Involved Techniques
Cloaking: The campaign employs cloaking to present different content based on the visitor's identity.
Search engine crawlers (e.g., Googlebot) are served fake government-style pages filled with SEO-optimized text, while real users are redirected to gambling or scam-related destinations. This dual behavior is key to evading detection.Keyword Stuffing: The malicious infrastructure pulls from a large keyword list and generates content that artificially boosts relevance for trending or popular search terms. These keywords are embedded into URLs, metadata, and page bodies to maximize visibility in search results.
Template-Based Content Generation: Using automation scripts, the server dynamically assembles fake pages using stitched-together news content, time-based tokens, and randomized keywords, all injected into reused HTML templates.
Hijacked Infrastructure: Legitimate subdomains of
.gov.brare exploited, allowing malicious pages to inherit domain authority and trust, significantly improving their rank in search engine results.System Vulnerabilities: Attackers appear to have exploited weaknesses in CMS or server configurations to host .html and .shtml files on compromised subdomains. However, the exact vulnerability being exploited has not yet been identified.
Technical Analysis
Infrastructure Overview
As revealed through Hunt.io IP intelligence insights, this section outlines the core server components, hosting details, and database structure powering the black hat SEO campaign.
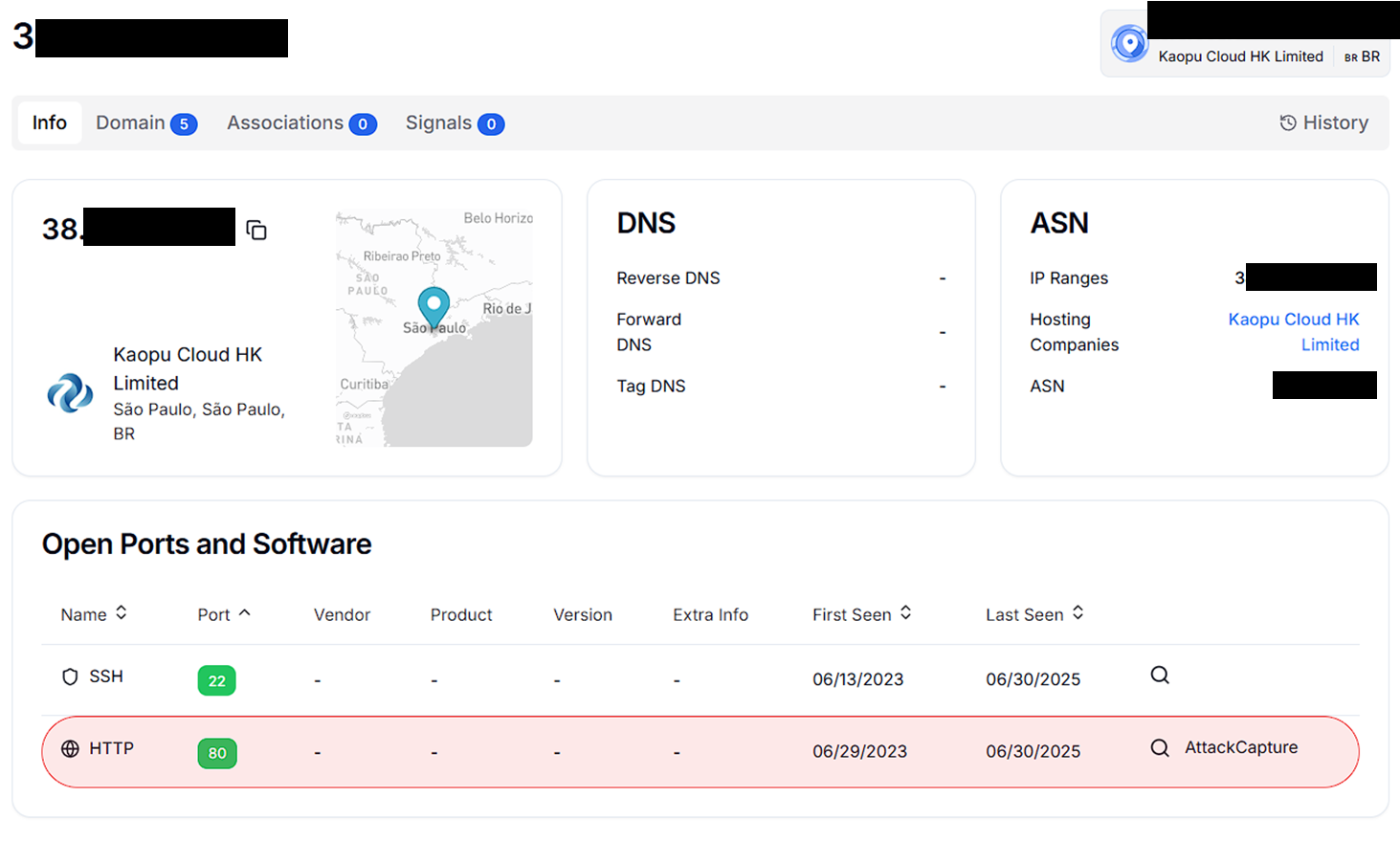 Figure 01. 3x.xx.xx.xx:xx IP Infrastructure information on the Hunt.io platform
Figure 01. 3x.xx.xx.xx:xx IP Infrastructure information on the Hunt.io platformIP Address:
3x.xx.xx.xx:80Hosting Provider: Kaopu Cloud HK Limited
Geographic Region: São Paulo, Brazil
Web Application: Flask-based server running on
0.0.0.0:8095Database Backend: MySQL
The server stores and serves dynamic SEO-optimized pages, using data from the following MySQL tables:
| Table Name | Purpose |
|---|---|
| keywords | Contains SEO keywords (used/unused flags) |
| news1, news2 | Store stitched or reused article content |
| govurl | Contains templated URLs with placeholders like {{type}} and {{keyword}} |
On this server, there were Python scripts that were used for URL generation, keyword stuffing, and cloaking.
Workflow Breakdown
Let's now explore how the Flask server processes incoming requests to generate SEO-manipulated content dynamically.
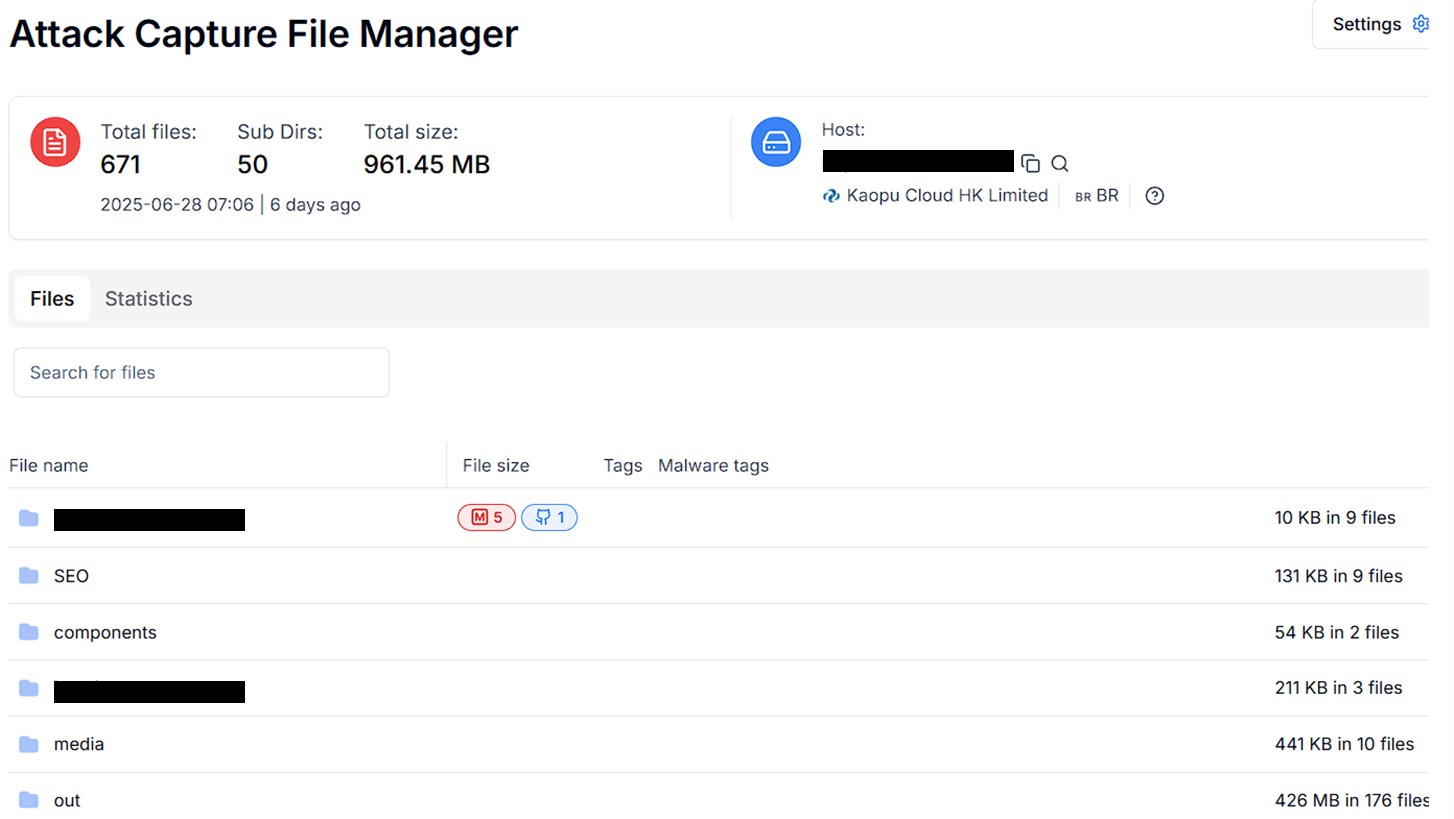 Figure. 02 Open Directories view using AttackCapture™ file manager
Figure. 02 Open Directories view using AttackCapture™ file manager1. /submit Endpoint Logic
Accepts
GET or
POST parameters:
https: Protocol selector (1 = HTTPS)ua: User-Agentformt: URL template (e.g.,abc.com/{{type}}/{{keyword}})keyword: Base keyword (e.g., "free games")dic (dictionary): Category string (e.g.,slotgames,bestsports)
2. Cloaking Mechanism
To avoid detection and manipulate search engine rankings, the threat actors employed cloaking, serving different content depending on whether the visitor was a search engine or a real user. The following diagram illustrates how this logic is implemented in the campaign's backend infrastructure.
 Fig. 03 AttackCapture™ code inspector displaying the exact line of code used for cloaking
Fig. 03 AttackCapture™ code inspector displaying the exact line of code used for cloakingGooglebot: Served dynamic, rich HTML content
Real users: Served a dummy "Loading..." page promoting
@Zad_Seoon Telegram
3. Content Assembly Process
Once a request is received, the server dynamically builds a search-optimized page using stitched content, keywords, and templated structures. This section explains how various database inputs and logic are combined to generate these deceptive pages.
If a bot/crawler is detected:
Pull 16 unused keywords from the keywords table and mark them as used
Generate:
innerurls: Based on the formt template and keywords
outerurls: Using random templates from govurl, replacing placeholders with keyword/category
Pull content from:
news1: Replace title occurrences with the target keyword
news2: Append stitched article content
Clean all HTML using regex (removet)
Split content into 6 balanced paragraphs
Fetch the current Brazil local time/date
Render using index.html with injected content
4. HTML Output
Let's now cover the final structure and components of the generated web pages, outlining how the assembled content, links, and keywords are presented in the rendered HTML to maximize SEO impact and deceive both search engines and users.
Page includes:
para1-para6: Fake article paragraphsinurl1-inurl9: Internally generated linksouturl1-outurl7: Externally styled.gov.br-like links redirecting to malicious sites.Main
keyword, SEO-optimized URL structure, and readable anchor text
Example Attack Flow
The following example demonstrates how a single user request gets transformed into a fake content page or a redirect, depending on the visitor type.
Request:
/submit?https=1&ua=Googlebot&formt=xx.com/{{type}}/{{keyword}}&keyword=casino-games&dic=slotgames
This request shows how the server detects a search engine crawler like Googlebot using the user-agent parameter and responds by generating a fully SEO-optimized page. It dynamically assembles keyword-rich content and links based on the provided parameters to boost search rankings. This cloaking technique ensures that crawlers see legitimate-looking pages, while real users are redirected to malicious sites, helping the campaign manipulate search results effectively.
Response (to Googlebot):
When the server detects a request from Googlebot, it responds with a fully rendered page containing multiple fake news paragraphs and numerous internal and external links optimized around the target keyword, creating the appearance of legitimate, relevant content to improve search engine rankings.
6 fake news paragraphs with "casino-games"
9 internal links like
https://xxx.-xx.xx.xxx7 external links like
https://xxx.xx.xxFully rendered HTML page with links injected
Response (to Real-User):
When a real user visits the page, instead of seeing the fake content shown to crawlers, they are immediately redirected to a betting or scam site, preventing them from accessing the deceptive SEO pages and funneling them toward malicious destinations.
They are redirected to a betting site or another malicious destination.
Component Analysis
Let's now break down the key components involved in content generation, templating, and subdomain abuse infrastructure.
Component 1: Flask App (app.py)
Using Hunt.io's AttackCapture™ tool, the core Flask application script (app.py) was identified as the central component responsible for generating dynamic content and implementing the cloaking mechanism. This script handles incoming requests, pulls data from the database, assembles SEO-optimized pages, and selectively serves different content to search engine crawlers and real users.
%2C+which+is+used+to+create+dynamic+content+and+a+cloaking+mechanism.png) Figure 0.4 AttackCapture™ code inspector showing app.py script, which is used to create dynamic content and a cloaking mechanism
Figure 0.4 AttackCapture™ code inspector showing app.py script, which is used to create dynamic content and a cloaking mechanismFunctionality:
The Flask application (app.py) serves as the main component responsible for generating dynamic, SEO-optimized content. It processes incoming requests, applies cloaking based on the user-agent, retrieves keywords and news content from the database, assembles the page using templates, and renders the final output delivering different content to search engine crawlers and real users.
Component 2: Index Template Preprocessor
Before the Flask app delivers content, the index template undergoes a preprocessing step that prepares it for dynamic content injection. Using Hunt.io's AttackCapture™ tool, we identified a helper script that refines the HTML by replacing placeholder tags with sequentially numbered variables and matching anchor text to keywords, ensuring the template remains flexible and scalable while evading detection patterns.
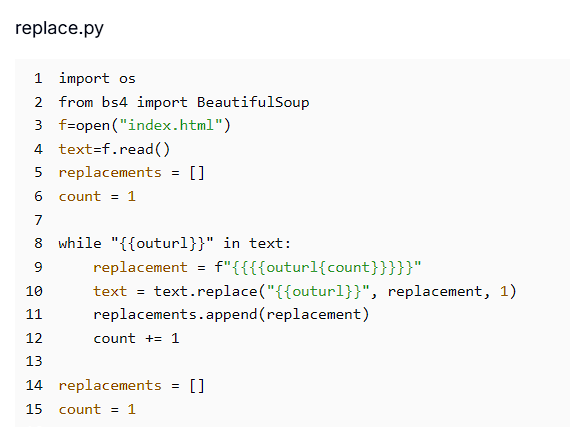 Figure 0.5: AttackCapture™ code inspector showing replace.py script, which is used to generate URLs with different keywords
Figure 0.5: AttackCapture™ code inspector showing replace.py script, which is used to generate URLs with different keywordsPrior to content delivery by the Flask application, the raw HTML template is processed by a helper script designed to enable dynamic content insertion. This script systematically replaces generic placeholders such as
{{inurl}}and{{outurl}}with sequentially numbered variables like inurl1, inurl2, and so forth, facilitating the inclusion of multiple distinct URLs on each page.Additionally, it maps anchor text placeholders (
{{inkeyX}},{{outkeyX}}) to their respective keywords, preserving content relevance. This preprocessing step ensures the template remains adaptable and scalable, supporting the creation of varied, SEO-friendly pages while minimizing repetitive elements that could lead to detection.
Component 3: index.txt (Cloned HTML Template)
The index.txt file serves as the cloned HTML template, originally taken from a legitimate .gov.br government page to lend authenticity to the fake sites. Using Hunt.io's AttackCapture™ tool, we uncovered how this template retains official branding, internal linking structures, and structured metadata (like JSON-LD), which attackers modify dynamically via the Flask backend to inject deceptive content and manipulate search engine rankings.
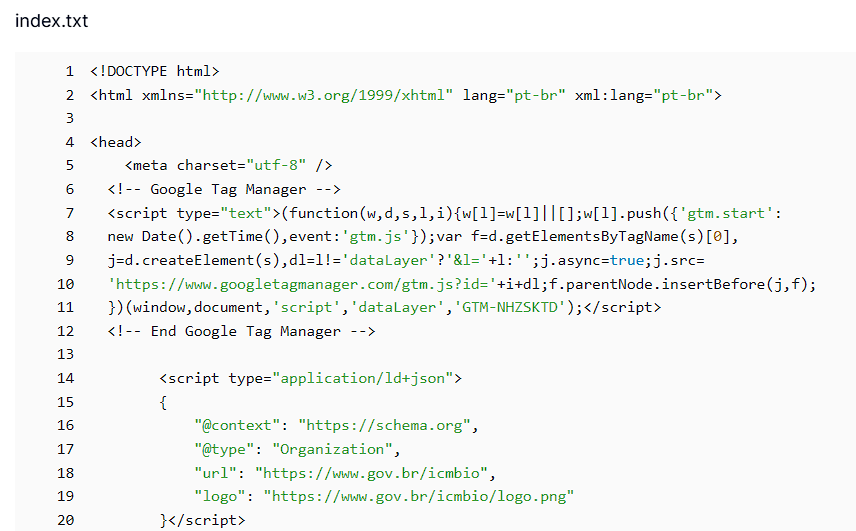 Figure 0.6 AttackCapture™ code inspector showing index.txt HTML page cloned from gov.br.
Figure 0.6 AttackCapture™ code inspector showing index.txt HTML page cloned from gov.br.The attackers cloned a legitimate HTML page from the .gov.br domain, preserving key elements such as government branding, internal links, and structured metadata like JSON-LD.
This authentic-looking template serves as a foundation to make the fake pages appear credible and trustworthy to both users and search engines. Using the Flask backend, the attackers then modify this template by injecting malicious or deceptive content, enabling the pages to effectively manipulate search rankings while maintaining a facade of legitimacy.
Campaign Flow
This section summarizes how the campaign creates and delivers deceptive content through hijacked subdomains and cloaking tactics. It starts with a cloned HTML template from a legitimate .gov.br site, embedded with dynamic placeholders.
The Flask server builds a fake page using keywords and content from its database. Search engine crawlers see this page, while real users are silently redirected to external scam destinations.
Output URLs
Here's how the generated URLs appeared based on the Python scripts used in the campaign.
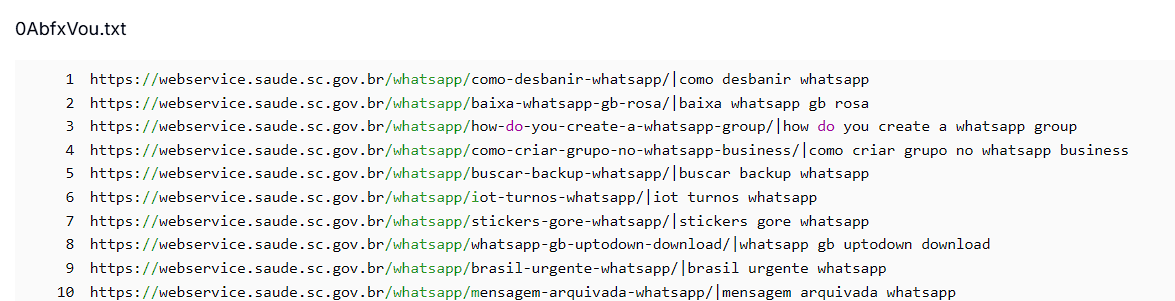 Figure 0.7 AttackCapture™ file viewer showing generated malicious URLs
Figure 0.7 AttackCapture™ file viewer showing generated malicious URLsThere were over 630k URLs generated using subdomains of gov.br, which are redirecting to betting sites, WhatsApp mod APK sites, etc.
Mitigations
For Authorities and Security Teams
Infrastructure Hardening
Enforce strict controls on file uploads to prevent unauthorized HTML/SHTML placement. Conduct regular scans for suspicious files and actively block script injection using robust input validation.
Website Monitoring
Routinely audit site content and outbound links. Set up monitoring for unexpected domain references and changes in search engine visibility. Leverage tools like Google Search Console to detect and disavow malicious backlinks.
For General Users
Awareness & Safe Browsing
Always double-check URLs, especially for government domains. Stay cautious of search results promoting gaming or unfamiliar platforms. Don't assume top-ranked results are trustworthy. Download apps only from verified stores.
Financial Safety
Avoid sharing banking details with unknown or unofficial websites. Be skeptical of high-return schemes or easy money promises. Refrain from engaging in unregulated online activities.
Public Outreach
Launch awareness campaigns about ongoing scams to foster informed, alert citizens. Provide clear channels for reporting suspicious content. Share advisories educating users on identifying and avoiding SEO-manipulated fraudulent platforms.
Final Thoughts
This campaign was not improvised. It was deliberately built to exploit trust at scale. By hijacking .gov.br subdomains and automating the creation of search-optimized pages, the attackers set up an infrastructure capable of quietly shaping what users see and where they end up.
The goal was not to break into systems. It was to control visibility. By tying malicious redirects to government domains, the attackers gained credibility without needing to exploit any user directly.
Operations like this often go unnoticed. They avoid triggering alerts because they rely on infrastructure that looks legitimate. To catch them early, defenders need to monitor for unusual patterns across trusted domains, not just look for known threats.
This campaign was uncovered using Hunt.io's AttackCapture™, which exposed the server, cloaking logic, and keyword automation behind the operation. If you're hunting similar infrastructure or need faster visibility into live threats, book a demo, and we'll show you how it works.
Indicators of Compromise (IOCs)
| Type | Value | Description |
|---|---|---|
| IP Address | 3x.xx.xxx.xx:xx | Server hosting the black hat SEO infrastructure |
| Hosting Provider | Kaopu Cloud HK Limited | Hosting provider used for malicious infrastructure |
| Telegram Handle | @Zad_Seo, @info_seo_team | Referenced in fake loading page shown to real users |
| Domain/Hostname | *.gov.br (Hijacked subdomains, full list available in the linked dataset) | Trusted infrastructure abused to host redirector pages |
| Hijacked Subdomain | https://xxx.xxx.xx/ | Example of hijacked subdomain redirecting to malicious content |
| Redirection Destination | https://xx.xx.xxx | Example redirection destination to malicious sites |

While investigating threats targeting Brazil and the broader South American region, we came across a suspicious server hosted at IP 3x.xx.xx.xx. What initially caught our attention was the volume of templated HTML files and Python scripts, which were clearly designed for large-scale automation.
Digging deeper, I realized this infrastructure was actively generating fake government-style pages by hijacking subdomains under
.gov.br. These pages were being used in a massive black hat SEO campaign to manipulate search engine results and redirect users to deceptive sites.
Please note that we have chosen to redact certain indicators in coordination with the Brazilian CTIR, as their investigation into this attack is still ongoing.
Executive Summary
Multiple subdomains under the Brazilian government's .gov.br domain have been hijacked and are currently being exploited to host or redirect to malicious websites.
These compromised subdomains are being used in a large-scale SEO poisoning campaign, where unsuspecting users searching online are funneled toward fraudulent gambling, betting, or scam pages.
Using Hunt.io's AttackCapture™ capability, we traced the infrastructure behind this operation to a single server hosting the full stack of automation scripts, templated HTML, and keyword manipulation tools fueling the campaign.
In this report, we will discuss the techniques used to mislead Brazilian Internet users when performing searches to clear their queries.
Campaign Overview
While searching for threats targeting the Brazilian region, analysts discovered a widespread SEO poisoning campaign exploiting hijacked subdomains under
.gov.br.
The discovery was made on 27th June 2025 using Hunt.io's AttackCapture™ feature, which surfaced an exposed server 38.xx.xx.xx:xx hosted by Kaopu Cloud HK Limited.
The server contained automation scripts, keyword databases, and templated HTML content used to generate thousands of fake, search-optimized URLs.
These URLs are served via compromised government infrastructure and are designed to redirect users to malicious or deceptive content, including gambling, betting, and investment-themed landing pages.
Search Engine Poisoning
Search Engine Poisoning (SEP) is a technique used by threat actors to manipulate search engine algorithms, causing malicious or misleading websites to appear among the top search results.
By mimicking legitimate content and abusing high-authority domains, attackers can redirect users searching for trustworthy information to fraudulent or harmful websites, often without their knowledge.
Involved Techniques
Cloaking: The campaign employs cloaking to present different content based on the visitor's identity.
Search engine crawlers (e.g., Googlebot) are served fake government-style pages filled with SEO-optimized text, while real users are redirected to gambling or scam-related destinations. This dual behavior is key to evading detection.Keyword Stuffing: The malicious infrastructure pulls from a large keyword list and generates content that artificially boosts relevance for trending or popular search terms. These keywords are embedded into URLs, metadata, and page bodies to maximize visibility in search results.
Template-Based Content Generation: Using automation scripts, the server dynamically assembles fake pages using stitched-together news content, time-based tokens, and randomized keywords, all injected into reused HTML templates.
Hijacked Infrastructure: Legitimate subdomains of
.gov.brare exploited, allowing malicious pages to inherit domain authority and trust, significantly improving their rank in search engine results.System Vulnerabilities: Attackers appear to have exploited weaknesses in CMS or server configurations to host .html and .shtml files on compromised subdomains. However, the exact vulnerability being exploited has not yet been identified.
Technical Analysis
Infrastructure Overview
As revealed through Hunt.io IP intelligence insights, this section outlines the core server components, hosting details, and database structure powering the black hat SEO campaign.
 Figure 01. 3x.xx.xx.xx:xx IP Infrastructure information on the Hunt.io platform
Figure 01. 3x.xx.xx.xx:xx IP Infrastructure information on the Hunt.io platformIP Address:
3x.xx.xx.xx:80Hosting Provider: Kaopu Cloud HK Limited
Geographic Region: São Paulo, Brazil
Web Application: Flask-based server running on
0.0.0.0:8095Database Backend: MySQL
The server stores and serves dynamic SEO-optimized pages, using data from the following MySQL tables:
| Table Name | Purpose |
|---|---|
| keywords | Contains SEO keywords (used/unused flags) |
| news1, news2 | Store stitched or reused article content |
| govurl | Contains templated URLs with placeholders like {{type}} and {{keyword}} |
On this server, there were Python scripts that were used for URL generation, keyword stuffing, and cloaking.
Workflow Breakdown
Let's now explore how the Flask server processes incoming requests to generate SEO-manipulated content dynamically.
 Figure. 02 Open Directories view using AttackCapture™ file manager
Figure. 02 Open Directories view using AttackCapture™ file manager1. /submit Endpoint Logic
Accepts
GET or
POST parameters:
https: Protocol selector (1 = HTTPS)ua: User-Agentformt: URL template (e.g.,abc.com/{{type}}/{{keyword}})keyword: Base keyword (e.g., "free games")dic (dictionary): Category string (e.g.,slotgames,bestsports)
2. Cloaking Mechanism
To avoid detection and manipulate search engine rankings, the threat actors employed cloaking, serving different content depending on whether the visitor was a search engine or a real user. The following diagram illustrates how this logic is implemented in the campaign's backend infrastructure.
 Fig. 03 AttackCapture™ code inspector displaying the exact line of code used for cloaking
Fig. 03 AttackCapture™ code inspector displaying the exact line of code used for cloakingGooglebot: Served dynamic, rich HTML content
Real users: Served a dummy "Loading..." page promoting
@Zad_Seoon Telegram
3. Content Assembly Process
Once a request is received, the server dynamically builds a search-optimized page using stitched content, keywords, and templated structures. This section explains how various database inputs and logic are combined to generate these deceptive pages.
If a bot/crawler is detected:
Pull 16 unused keywords from the keywords table and mark them as used
Generate:
innerurls: Based on the formt template and keywords
outerurls: Using random templates from govurl, replacing placeholders with keyword/category
Pull content from:
news1: Replace title occurrences with the target keyword
news2: Append stitched article content
Clean all HTML using regex (removet)
Split content into 6 balanced paragraphs
Fetch the current Brazil local time/date
Render using index.html with injected content
4. HTML Output
Let's now cover the final structure and components of the generated web pages, outlining how the assembled content, links, and keywords are presented in the rendered HTML to maximize SEO impact and deceive both search engines and users.
Page includes:
para1-para6: Fake article paragraphsinurl1-inurl9: Internally generated linksouturl1-outurl7: Externally styled.gov.br-like links redirecting to malicious sites.Main
keyword, SEO-optimized URL structure, and readable anchor text
Example Attack Flow
The following example demonstrates how a single user request gets transformed into a fake content page or a redirect, depending on the visitor type.
Request:
/submit?https=1&ua=Googlebot&formt=xx.com/{{type}}/{{keyword}}&keyword=casino-games&dic=slotgames
This request shows how the server detects a search engine crawler like Googlebot using the user-agent parameter and responds by generating a fully SEO-optimized page. It dynamically assembles keyword-rich content and links based on the provided parameters to boost search rankings. This cloaking technique ensures that crawlers see legitimate-looking pages, while real users are redirected to malicious sites, helping the campaign manipulate search results effectively.
Response (to Googlebot):
When the server detects a request from Googlebot, it responds with a fully rendered page containing multiple fake news paragraphs and numerous internal and external links optimized around the target keyword, creating the appearance of legitimate, relevant content to improve search engine rankings.
6 fake news paragraphs with "casino-games"
9 internal links like
https://xxx.-xx.xx.xxx7 external links like
https://xxx.xx.xxFully rendered HTML page with links injected
Response (to Real-User):
When a real user visits the page, instead of seeing the fake content shown to crawlers, they are immediately redirected to a betting or scam site, preventing them from accessing the deceptive SEO pages and funneling them toward malicious destinations.
They are redirected to a betting site or another malicious destination.
Component Analysis
Let's now break down the key components involved in content generation, templating, and subdomain abuse infrastructure.
Component 1: Flask App (app.py)
Using Hunt.io's AttackCapture™ tool, the core Flask application script (app.py) was identified as the central component responsible for generating dynamic content and implementing the cloaking mechanism. This script handles incoming requests, pulls data from the database, assembles SEO-optimized pages, and selectively serves different content to search engine crawlers and real users.
%2C+which+is+used+to+create+dynamic+content+and+a+cloaking+mechanism.png) Figure 0.4 AttackCapture™ code inspector showing app.py script, which is used to create dynamic content and a cloaking mechanism
Figure 0.4 AttackCapture™ code inspector showing app.py script, which is used to create dynamic content and a cloaking mechanismFunctionality:
The Flask application (app.py) serves as the main component responsible for generating dynamic, SEO-optimized content. It processes incoming requests, applies cloaking based on the user-agent, retrieves keywords and news content from the database, assembles the page using templates, and renders the final output delivering different content to search engine crawlers and real users.
Component 2: Index Template Preprocessor
Before the Flask app delivers content, the index template undergoes a preprocessing step that prepares it for dynamic content injection. Using Hunt.io's AttackCapture™ tool, we identified a helper script that refines the HTML by replacing placeholder tags with sequentially numbered variables and matching anchor text to keywords, ensuring the template remains flexible and scalable while evading detection patterns.
 Figure 0.5: AttackCapture™ code inspector showing replace.py script, which is used to generate URLs with different keywords
Figure 0.5: AttackCapture™ code inspector showing replace.py script, which is used to generate URLs with different keywordsPrior to content delivery by the Flask application, the raw HTML template is processed by a helper script designed to enable dynamic content insertion. This script systematically replaces generic placeholders such as
{{inurl}}and{{outurl}}with sequentially numbered variables like inurl1, inurl2, and so forth, facilitating the inclusion of multiple distinct URLs on each page.Additionally, it maps anchor text placeholders (
{{inkeyX}},{{outkeyX}}) to their respective keywords, preserving content relevance. This preprocessing step ensures the template remains adaptable and scalable, supporting the creation of varied, SEO-friendly pages while minimizing repetitive elements that could lead to detection.
Component 3: index.txt (Cloned HTML Template)
The index.txt file serves as the cloned HTML template, originally taken from a legitimate .gov.br government page to lend authenticity to the fake sites. Using Hunt.io's AttackCapture™ tool, we uncovered how this template retains official branding, internal linking structures, and structured metadata (like JSON-LD), which attackers modify dynamically via the Flask backend to inject deceptive content and manipulate search engine rankings.
 Figure 0.6 AttackCapture™ code inspector showing index.txt HTML page cloned from gov.br.
Figure 0.6 AttackCapture™ code inspector showing index.txt HTML page cloned from gov.br.The attackers cloned a legitimate HTML page from the .gov.br domain, preserving key elements such as government branding, internal links, and structured metadata like JSON-LD.
This authentic-looking template serves as a foundation to make the fake pages appear credible and trustworthy to both users and search engines. Using the Flask backend, the attackers then modify this template by injecting malicious or deceptive content, enabling the pages to effectively manipulate search rankings while maintaining a facade of legitimacy.
Campaign Flow
This section summarizes how the campaign creates and delivers deceptive content through hijacked subdomains and cloaking tactics. It starts with a cloned HTML template from a legitimate .gov.br site, embedded with dynamic placeholders.
The Flask server builds a fake page using keywords and content from its database. Search engine crawlers see this page, while real users are silently redirected to external scam destinations.
Output URLs
Here's how the generated URLs appeared based on the Python scripts used in the campaign.
 Figure 0.7 AttackCapture™ file viewer showing generated malicious URLs
Figure 0.7 AttackCapture™ file viewer showing generated malicious URLsThere were over 630k URLs generated using subdomains of gov.br, which are redirecting to betting sites, WhatsApp mod APK sites, etc.
Mitigations
For Authorities and Security Teams
Infrastructure Hardening
Enforce strict controls on file uploads to prevent unauthorized HTML/SHTML placement. Conduct regular scans for suspicious files and actively block script injection using robust input validation.
Website Monitoring
Routinely audit site content and outbound links. Set up monitoring for unexpected domain references and changes in search engine visibility. Leverage tools like Google Search Console to detect and disavow malicious backlinks.
For General Users
Awareness & Safe Browsing
Always double-check URLs, especially for government domains. Stay cautious of search results promoting gaming or unfamiliar platforms. Don't assume top-ranked results are trustworthy. Download apps only from verified stores.
Financial Safety
Avoid sharing banking details with unknown or unofficial websites. Be skeptical of high-return schemes or easy money promises. Refrain from engaging in unregulated online activities.
Public Outreach
Launch awareness campaigns about ongoing scams to foster informed, alert citizens. Provide clear channels for reporting suspicious content. Share advisories educating users on identifying and avoiding SEO-manipulated fraudulent platforms.
Final Thoughts
This campaign was not improvised. It was deliberately built to exploit trust at scale. By hijacking .gov.br subdomains and automating the creation of search-optimized pages, the attackers set up an infrastructure capable of quietly shaping what users see and where they end up.
The goal was not to break into systems. It was to control visibility. By tying malicious redirects to government domains, the attackers gained credibility without needing to exploit any user directly.
Operations like this often go unnoticed. They avoid triggering alerts because they rely on infrastructure that looks legitimate. To catch them early, defenders need to monitor for unusual patterns across trusted domains, not just look for known threats.
This campaign was uncovered using Hunt.io's AttackCapture™, which exposed the server, cloaking logic, and keyword automation behind the operation. If you're hunting similar infrastructure or need faster visibility into live threats, book a demo, and we'll show you how it works.
Indicators of Compromise (IOCs)
| Type | Value | Description |
|---|---|---|
| IP Address | 3x.xx.xxx.xx:xx | Server hosting the black hat SEO infrastructure |
| Hosting Provider | Kaopu Cloud HK Limited | Hosting provider used for malicious infrastructure |
| Telegram Handle | @Zad_Seo, @info_seo_team | Referenced in fake loading page shown to real users |
| Domain/Hostname | *.gov.br (Hijacked subdomains, full list available in the linked dataset) | Trusted infrastructure abused to host redirector pages |
| Hijacked Subdomain | https://xxx.xxx.xx/ | Example of hijacked subdomain redirecting to malicious content |
| Redirection Destination | https://xx.xx.xxx | Example redirection destination to malicious sites |
Related Posts:
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.